gray-wolf-analysis
大灰狼远控分析
主要是C++反汇编与逆向分析的几个木马分析流程,自己做一做。大灰狼远控木马是一个比较常见的远控工具。
初步分析
有两个文件:Consys21与SB360,发现是VC6写的,其中前者是dll,后者是exe。查看Winmain,发现一直调用sleep函数,这是病毒干扰杀毒软件查杀的方式,如下所示:
启动过程分析
首先对数据进行解密。
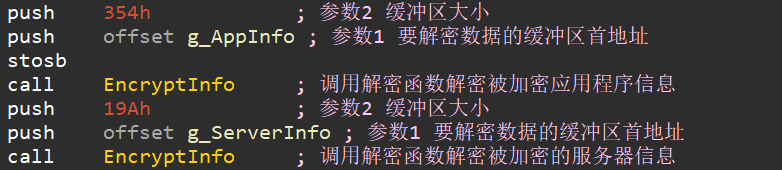
其中,EncryptInfo的函数实现如下:
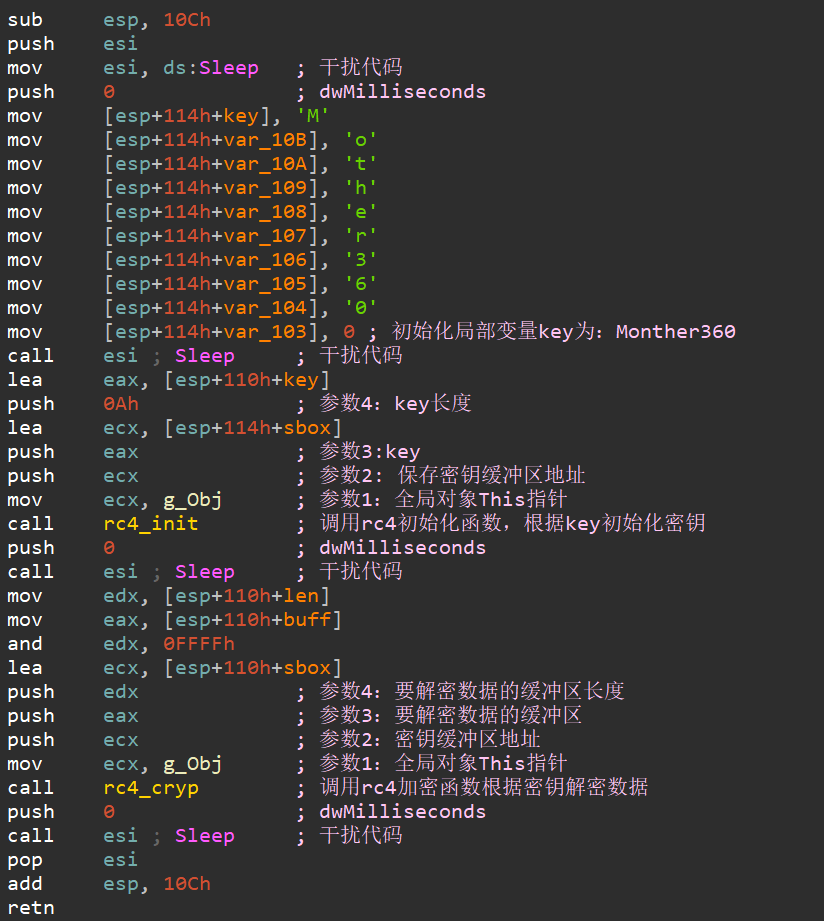
可以发现,将key赋值为Monther360,并调用rc4解密。解密后,可以得到:
1 | g_AppInfo : SuperProServer |
接着分析:
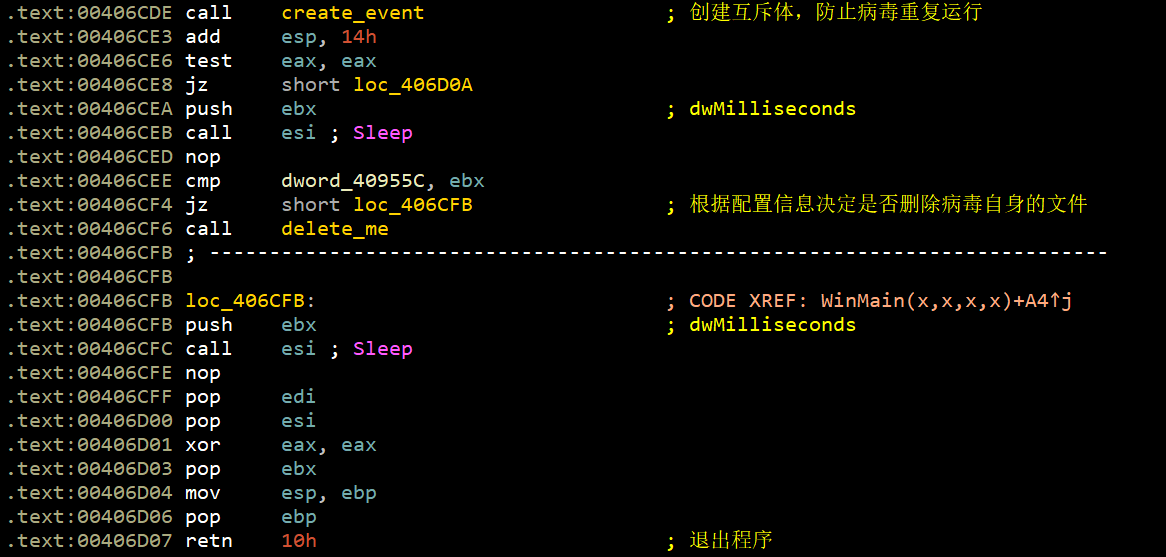
正常状态是跳转到loc_406D0A,如下所示:
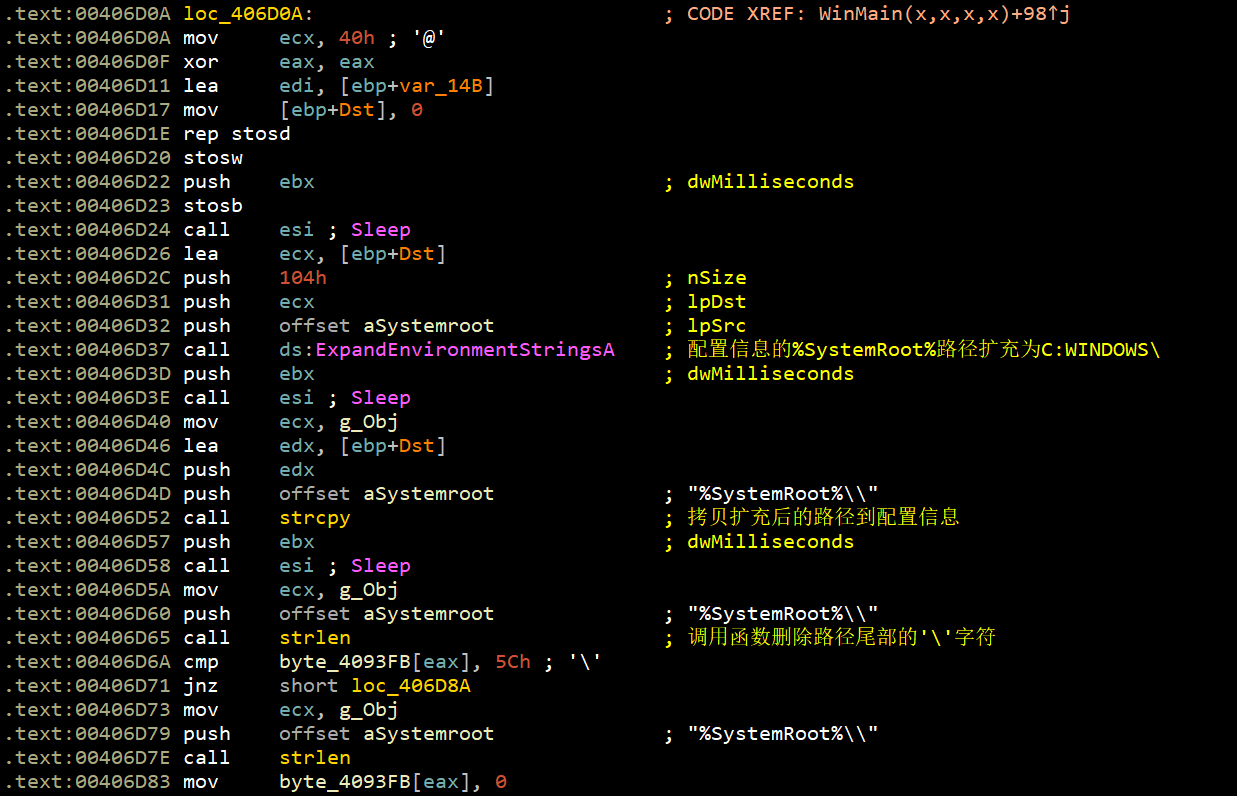
上面这段代码是处理路径用的。接着,运行:
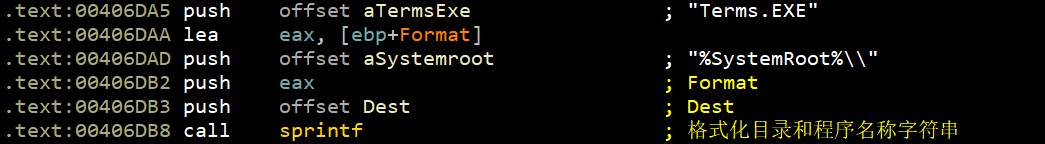

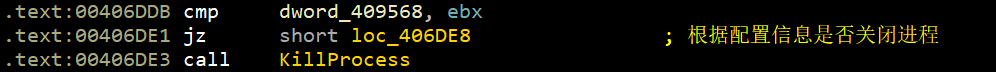
后续反汇编不再展示,直接上代码:
1 | int __stdcall WinMain(HINSTANCE hInstance, HINSTANCE hPrevInstance, LPSTR lpCmdLine, int nShowCmd) |
再来看run_main:
1 | int run_main() |
总结一下,上述代码首先根据解密后配置的信息决定病毒的启动方式:直接启动、通过服务启动、修改注册表开机启动,之后读取与保存注册表信息,进入run_main。在run_main中,根据配置信息决定是否以独占方式运行,从而使得病毒无法被删除。独占方式原理如下:
(1)通过AdjustTokenPrivileges提权。
(2)通过OpenProcess打开system进程。
(3)通过CreateFile打开独占大文件句柄。
(4)通过DuplicateHandle将文件句柄复制到system进程中。
之后,运行socket_main函数,与服务器进行通信。如下所示:
1 | int socket_main() |
可以看到,病毒初始化了socket,并在connect_server函数中,查询DNS服务器,根据域名转换地址,并接收远端发来的数据。
通信协议分析
在connect_server中,有线程回调函数recv_proc函数,跟踪一下。
1 | signed int __stdcall recv_proc(SOCKET *a1) |
不难发现,所有的接收数据都使用RC4加密,解密后用parse_data进行分割。在parse_data中,使用虚函数parse_command进行进一步处理。通过分析,协议格式为:5字节头部标志,4字节原始数据大小,4字节压缩后数据大小,1字节命令,变长数据,4字节压缩标志。
1 | void __thiscall parse_command(int this, const CHAR *a2, int a3) |
通过parse_command,可以看到此木马包括多种功能,包括屏幕查看、摄像头查看、语音监控、卸载等。
远控功能分析
在所有功能中(dllFile、dllShell、dllAudio等),都运行了共同的函数load_run_control。经过分析,该病毒为了隐秘的运行插件的核心代码,会先从远程服务器下载插件动态库。之后动态申请内存,模拟PE装载流程(未使用LoadLibrary,而是自己写的load_pe),将恶意代码加载入内存。最后,通过自己模拟的GetProcAddress(叫做get_proc_adddres),调用动态库的导出函数。动态库的文件格式做了加密,并修改了PE文件的前两个字节,不同的变种病毒会采用不同的加密方式。
将库下载并分析,其中语音监控如下:
1 | int __cdecl DllAudio(int a1, char *name, u_short hostshort, const char *a4) |
其余的攻击实现,可以看书P549左右,在此不再多说。
留言
- 文章链接: https://wd-2711.tech/
- 版权声明: 本博客所有文章除特别声明外,均采用 CC BY-NC-ND 4.0 许可协议。转载请注明出处!